Biztonsági szemle

2025. Már. 26.
Biztonsági szemle
Unlocking the Power of Network Telemetry for the US Public Sector
Co-authors: Lou Norman and Erich Stokes A golden nugget can be seen as a valuable piece of information that significantly enhances security measures. In cybersecurity, identifying and leveraging such golden nuggets can be crucial for maintaining...

2025. Már. 26.
Biztonsági szemle
The Benefits of a Broad and Open Integration Ecosystem
Since inception, Cisco XDR has followed the Open XDR philosophy. We integrate telemetry and data from dozens of Cisco and third-party security solutions.

2025. Már. 26.
Biztonsági szemle
Google Hastily Patches Chrome Zero-Day Exploited by APT
Researchers at Kaspersky discovered cyber-espionage activity that used the vulnerability in a one-click phishing attack to deliver malware.

2025. Már. 26.
Biztonsági szemle
Public-Private Ops Net Big Wins Against African Cybercrime
Three cybersecurity firms worked with Interpol and authorities in Nigeria, South Africa, Rwanda, and four other African nations to arrest more than 300 cybercriminals.

2025. Már. 26.
Biztonsági szemle
ISC Stormcast For Wednesday, March 26th, 2025 https://isc.sans.edu/podcastdetail/9380, (Wed, Mar 26th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
2025. Már. 26.
Biztonsági szemle
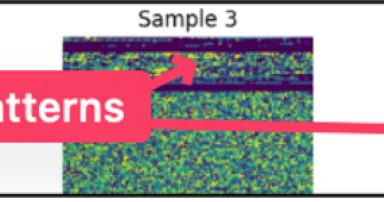
[Guest Diary] Leveraging CNNs and Entropy-Based Feature Selection to Identify Potential Malware Artifacts of Interest, (Wed, Mar 26th)
[This is a Guest Diary by Wee Ki Joon, an ISC intern as part of the SANS.edu Bachelor's Degree in Applied Cybersecurity (BACS) program [1].]

2025. Már. 25.
Biztonsági szemle
Chinese hackers spend years roaming telecommunications service
China Chopper malware allowed threat group "Weaver Ant" to remain undetected for years.

2025. Már. 25.
Biztonsági szemle
Security Tech That Can Make a Difference During an Attack
The recent report of how Volt Typhoon compromised systems at a water utility highlight security technologies and processes that helped detect the compromise and clean up the network.

2025. Már. 25.
Biztonsági szemle
Security Tech That Can Make a Difference During an Attack
The recent report of how Volt Typhoon compromised systems at a water utility highlight security technologies and processes that helped detect the compromise and clean up the network.

2025. Már. 25.
Biztonsági szemle
Curdled Miscreant, VanHelsing, MFA, Room 237, MFA, Velora, 23nMe, Josh Marpet... - SWN #462

2025. Már. 25.
Biztonsági szemle
OPSEC Nightmare: Leaking US Military Plans to a Reporter
Experts say the leakage of US military plans to a reporter this month reflects a severe operational security failure on the part of US leadership.

2025. Már. 25.
Biztonsági szemle
South African Poultry Company Reports $1M Loss After Cyber Intrusion
The company reports that no sensitive information was breached or stolen in the cyber intrusion and that its operations are running normally again.
Oldalszámozás
- Előző oldal ‹‹
- 289. oldal
- Következő oldal ››