Biztonsági szemle

2024. Okt. 18.
Biztonsági szemle
Vulnerabilities, AI Compete for Software Developers' Attention
This year, the majority of developers have adopted AI assistants to help with coding and improve code output, but most are also creating more vulnerabilities that take longer to remediate.

2024. Okt. 18.
Biztonsági szemle
Bell Canada’s Transformation Journey with Routed Optical Networking
Jason Teller sat down with Marc-André Gilbert, Senior Manager of Transport Planning at Bell Canada, to hear about the company’s network transformation journey using Routed Optical Networking and how it will enable Bell Canada to fulfill its strategic...

2024. Okt. 18.
Biztonsági szemle
Microsoft customer security logs misplaced due to vulnerability
Impacted by different levels of log disruption were Microsoft Entra, Microsoft Sentinel, Azure Logic Apps, Azure Monitor, Azure Healthcare APIs, Azure Trusted Signing, Azure Virtual Desktop, and Power Platform, according to Microsoft.
2024. Okt. 18.
Biztonsági szemle
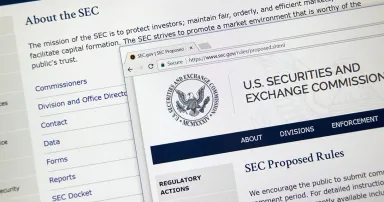
US arrests, indicts hacker of SEC's X account
Such a breach was conducted through SIM swapping, with Eric Council Jr., also known as Easymunny, Ronin, and AGiantSchnauzer, and his co-conspirators crafting a false identity using information from a third party with access to SEC's X account, the...

2024. Okt. 18.
Biztonsági szemle
Casio ransomware recovery remains bleak
Immediate action to contain the intrusion via server takedowns has affected shipments although only Japanese customers are believed to be impacted by such issues.

2024. Okt. 18.
Biztonsági szemle
BianLian admits responsibility for Boston Children's Health Physicians hack
In a post on its extortion portal earlier this week, BianLian alleged the theft of BCHP's emails, finance and HR data, personally identifiable information and health records, database dumps, health insurance records, and child-related data although...

2024. Okt. 18.
Biztonsági szemle
Globe Life extorted following subsidiary breach
Information compromised as a result of the incident included individuals' names, addresses, Social Security numbers, and health-related details, among others although a probe into the total extent of stolen data continues, said Globe Life in a filing...

2024. Okt. 18.
Biztonsági szemle
Infostealers deployed via phony Google Meet alerts
Attacks involved the display of fraudulent Google Meet popup alerts, which would download the StealC or Rhadamanthys infostealers for Windows users and the AMOS Stealer payload for macOS users, according to a Sekoia analysis.

2024. Okt. 18.
Biztonsági szemle
Supply Chain Cybersecurity Beyond Traditional Vendor Risk Management
Traditional practices are no longer sufficient in today's threat landscape. It's time for cybersecurity professionals to rethink their approach.

2024. Okt. 18.
Biztonsági szemle
Tájékoztató az iráni kibercsoportok kritikus infrastruktúrát támadó tevékenységéről
A Nemzetbiztonsági Szakszolgálat Nemzeti Kibervédelmi Intézete tájékoztatót ad ki iráni kibercsoportok destruktív, a kritikus infrastruktúrát célzó támadásaival kapcsolatban.

2024. Okt. 18.
Biztonsági szemle
Sajtószemle – 2024. 42. hét
A 2024. 42. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2024.10.11. és 2024.10.17. között kezelt incidensek statisztikai adatait is tartalmazza.
Oldalszámozás
- Előző oldal ‹‹
- 534. oldal
- Következő oldal ››