Biztonsági szemle
2024. Okt. 15.
Biztonsági szemle
Guidance: Framing Software Component Transparency: Establishing a Common Software Bill of Materials (SBOM)
Today, CISA published the Framing Software Component Transparency , created by the Software Bill of Materials (SBOM) Tooling & Implementation Working Group, one of the five SBOM community-driven workstreams facilitated by CISA. CISA’s community...
2024. Okt. 15.
Biztonsági szemle
Schneider Electric Data Center Expert
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.6 ATTENTION: Exploitable remotely/low attack complexity Vendor: Schneider Electric Equipment: Data Center Expert Vulnerability: Improper Verification of Cryptographic Signature, Missing Authentication for...

2024. Okt. 15.
Biztonsági szemle
What the US can learn from the UK and EU about regulating AI
There are ways to protect the public from the potential dangers of AI without stifling innovation – and the Europeans have already shown us how.
2024. Okt. 15.
Biztonsági szemle
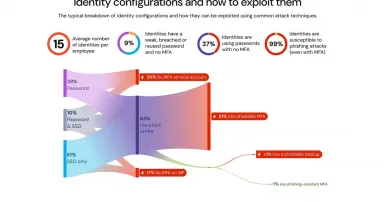
Even Orgs With SSO Are Vulnerable to Identity-Based Attacks
Use SSO, don't use SSO. Have MFA, don't have MFA. An analysis of a snapshot of organizations using Push Security's platform finds that 99% of accounts susceptible to phishing attacks.

2024. Okt. 15.
Biztonsági szemle
ISC Stormcast For Tuesday, October 15th, 2024 https://isc.sans.edu/podcastdetail/9180, (Tue, Oct 15th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

2024. Okt. 15.
Biztonsági szemle
Southeast Asian Cybercrime Profits Fuel Shadow Economy
With cybercriminal gangs raking in at least $18 billion regionally — and much more globally — law enforcement and policymakers are struggling to keep up as the syndicates innovate and entrench themselves in national economies.

2024. Okt. 15.
Biztonsági szemle
Serious Adversaries Circle Ivanti CSA Zero-Day Flaws
Suspected nation-state actors are spotted stringing together three different zero-days in the Ivanti Cloud Services Application to gain persistent access to a targeted system.

2024. Okt. 14.
Biztonsági szemle
Pentagon shares new cybersecurity rules for government contractors
The DOD introduced new cybersecurity requirements for companies that contract with the federal government.

2024. Okt. 14.
Biztonsági szemle
Pokémon Gaming Company Employee Info Leaked in Hack
The gaming company reports that the server has been rebuilt after the leak, but has not confirmed if its insider video game data was leaked.

2024. Okt. 14.
Biztonsági szemle
The Lingering 'Beige Desktop' Paradox
Organizations are grappling with the risks of having outdated hardware handling core workloads, mission-critical applications no one knows how to update or maintain, and systems that IT and security teams don't know about.

2024. Okt. 14.
Biztonsági szemle
Microsoft: Schools Grapple With Thousands of Cyberattacks Weekly
Education, including K-12 schools and universities, has become the third most targeted sector due to the high variety of sensitive data it stores in its databases.
2024. Okt. 14.
Biztonsági szemle
Vulnerable instances of Log4j still being used nearly 3 years later
Critical vulnerabilities take over 500 days to be fixed.
Oldalszámozás
- Előző oldal ‹‹
- 542. oldal
- Következő oldal ››