Biztonsági szemle

2026. Jan. 30.
Biztonsági szemle
2026: The Year Agentic AI Becomes the Attack-Surface Poster Child
Dark Reading asked readers whether agentic AI attacks, advanced deepfake threats, board recognition of cyber as a top priority, or password-less technology adoption would be most likely to become a trending reality for 2026.

2026. Jan. 30.
Biztonsági szemle
Out-of-the-Box Expectations for 2026 Reveal a Grab-Bag of Risk
Security teams need to be thinking about this list of emerging cybersecurity realities, to avoid rolling the dice on enterprise security risks (and opportunities).

2026. Jan. 30.
Biztonsági szemle
Tenable Tackles AI Governance, Shadow AI Risks, Data Exposure
The Tenable One AI Exposure add-on discovers unsanctioned AI use in the organization and enforces policy compliance with approved tools.
2026. Jan. 30.
Biztonsági szemle
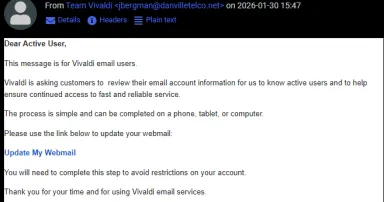
Google Presentations Abused for Phishing, (Fri, Jan 30th)
Charlie, one of our readers, has forwarded an interesting phishing email. The email was sent to users of the Vivladi Webmail service. While not overly convincing, the email is likely sufficient to trick a non-empty group of users:

2026. Jan. 30.
Biztonsági szemle
OpenClaw AI Runs Wild in Business Environments
The popular open source AI assistant (aka ClawdBot, MoltBot) has taken off, raising security concerns over its privileged, autonomous control within users' computers.

2026. Jan. 30.
Biztonsági szemle
Sajtószemle – 2026. 5. hét
Megjelent a 2026. 5. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2026.01.23. és 2026.01.29. között kezelt incidensek, valamint az elosztott kormányzati IT biztonsági csapdarendszerből (GovProbe1) származó adatok statisztikai eloszlását is...

2026. Jan. 30.
Biztonsági szemle
ISC Stormcast For Friday, January 30th, 2026 https://isc.sans.edu/podcastdetail/9788, (Fri, Jan 30th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

2026. Jan. 30.
Biztonsági szemle
Chinese APTs Hacking Asian Orgs With High-End Malware
Advanced persistent threat (APT) groups have deployed new cyber weapons against a variety of targets, highlighting the increasing threats to the region.

2026. Jan. 29.
Biztonsági szemle
Trump Administration Rescinds Biden-Era SBOM Guidance
Federal agencies will no longer be required to solicit software bills of material (SBOMs) from tech vendors, nor attestations that they comply with NIST's Secure Software Development Framework (SSDF). What that means long term is unclear.

2026. Jan. 29.
Biztonsági szemle
More Critical Flaws on n8n Could Compromise Customer Security
A new around of vulnerabilities in the popular AI automation platform could let attackers hijack servers and steal credentials.

2026. Jan. 29.
Biztonsági szemle
MCP and A2A: A Network Engineer’s Mental Model for Agentic AI
The Model Context Protocol (MCP) and Agent-to-Agent (A2A) have gained a significant industry attention over the past year. MCP first grabbed the world’s attention in dramatic fashion when it was published by Anthropic in November 2024, garnering tens...

2026. Jan. 29.
Biztonsági szemle
TAG Bulletin: Q4 2025
An overview of coordinated influence operation campaigns terminated on our platforms in Q4 2025.
Oldalszámozás
- Előző oldal ‹‹
- 9. oldal
- Következő oldal ››