Security Bulletin
5 Aug 2025
Biztonsági szemle
Stealing Machine Keys for fun and profit (or riding the SharePoint wave), (Tue, Aug 5th)
About 10 days ago exploits for Microsoft SharePoint (CVE-2025-53770, CVE-2025-53771) started being publicly abused â we wrote about that at here and here .

5 Aug 2025
Biztonsági szemle
Google Chrome Enterprise: More Than an Access Point to the Web
In a conversation with Dark Reading's Terry Sweeney, Lauren Miskelly from Google explains that Chrome Enterprise is the same Chrome browser that consumers use, but with additional enterprise-grade controls, reporting capabilities, and administrative...

5 Aug 2025
Biztonsági szemle
ISC Stormcast For Tuesday, August 5th, 2025 https://isc.sans.edu/podcastdetail/9556, (Tue, Aug 5th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

5 Aug 2025
Biztonsági szemle
Minimal, Hardened, and Updated Daily: The New Standard for Secure Containers
Chainguard provides DevSecOps teams with a library of "secure-by-default" container images so that they don't have to worry about software supply chain vulnerabilities. The startup is expanding its focus to include Java and Linux, as well.

4 Aug 2025
Biztonsági szemle
Nvidia Patches Critical RCE Vulnerability Chain
The flaws in the company's Triton Inference Server enables model theft, data leaks, and response manipulation.

4 Aug 2025
Biztonsági szemle
CISA & FEMA Announce $100M+ in Community Cybersecurity Grants
The grants are intended to help states, tribes, and localities enhance their cybersecurity resilience by providing them with monetary resources to reduce risks and implement new procedures.

4 Aug 2025
Biztonsági szemle
MacOS Under Attack: How Organizations Can Counter Rising Threats
Not only are attacks against macOS users ramping up, but threat actors have proved to be advanced with deepfake technology. Security awareness training may be the best defense.

4 Aug 2025
Biztonsági szemle
Threat Actors Increasingly Leaning on GenAI Tools
From "eCrime" actors to fake IT tech workers, CrowdStrike researchers found that adversaries are using AI to enhance their offensive cyber operations.

4 Aug 2025
Biztonsági szemle
42% of Developers Using AI Say Their Codebase is Now Mostly AI-Generated
4 Aug 2025
Biztonsági szemle
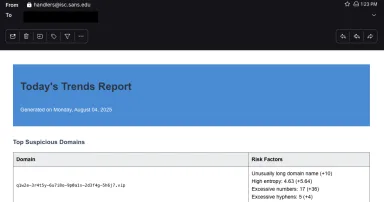
New Feature: Daily Trends Report, (Mon, Aug 4th)
I implemented a new report today, the "Daily Trends" report. It summarizes noteworthy data received from our honeypot. As with everything, it will improve if you provide feedback :)

4 Aug 2025
Biztonsági szemle
How Nestlé Revamped Its Network for Resilience and Efficiency
Learn how updating to Cisco SD-WAN, Cisco ThousandEyes, and Cisco Secure Routers helped Nestlé manage its global network with greater efficiency and resilience.
Pagination
- Previous page ‹‹
- Page 102
- Next page ››