Security Bulletin

16 Jul 2025
Biztonsági szemle
Highlights for Consumer Industries from Cisco Live US 2025
IT leaders from across the country gathered at Cisco Live US 2025 to explore the latest innovations, strategies, and best practices in technology. The event featured tailored sessions and keynotes designed to address the unique challenges and...

16 Jul 2025
Biztonsági szemle
Securing the Budget: Demonstrating Cybersecurity's Return
By tying security investments to measurable outcomes — like reduced breach likelihood and financial impact — CISOs can align internal stakeholders and justify spending based on real-world risk.
16 Jul 2025
Biztonsági szemle
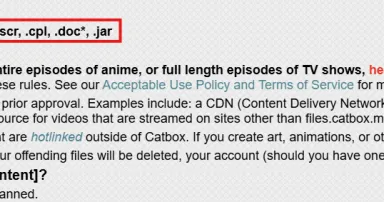
More Free File Sharing Services Abuse, (Wed, Jul 16th)
A few months ago, I wrote a diary about online services used to exfiltrate data[ 1]. In this diary, I mentioned some well-known services. One of them was catbox.moe[ 2]. Recently, I found a sample that was trying to download some payload from this...

16 Jul 2025
Biztonsági szemle
CVE-2025-40776: Birthday Attack against Resolvers supporting ECS
CVE: CVE-2025-40776 Title: Birthday Attack against Resolvers supporting ECS Document version: 2.0 Posting date: 16 July 2025 Program impacted: BIND 9 Versions affected: BIND Supported Preview Edition 9.11.3-S1 -> 9.16.50-S1 9.18.11-S1 -> 9.18.37-S1 9...

16 Jul 2025
Biztonsági szemle
Cybersecurity in Healthcare Needs a Profound Rethink
This blog explores why healthcare is so attractive for cybercriminals and outlines five actions to reset how we approach security in the sector with a long-term comprehensive vision enabling organizations to build long-term resilience.

16 Jul 2025
Biztonsági szemle
ISC Stormcast For Wednesday, July 16th, 2025 https://isc.sans.edu/podcastdetail/9528, (Wed, Jul 16th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

16 Jul 2025
Biztonsági szemle
Altered Telegram App Steals Chinese Users' Android Data
Using more than 600 domains, attackers entice Chinese-speaking victims to download a vulnerable Telegram app that is nearly undetectable on older versions of Android.

16 Jul 2025
Biztonsági szemle
Meet Belkie: Your 45-Second CCNA Certification Coach
Prepping for the CCNA? This new series will walk you through all the things you didn't know you didn't know.

15 Jul 2025
Biztonsági szemle
ISC2 Finds Orgs Are Increasingly Leaning on AI
While many organizations are eagerly integrating AI into their workflows and cybersecurity practices, some remain undecided and even concerned about potential drawbacks of AI deployment.

15 Jul 2025
Biztonsági szemle
Lessons Learned From McDonald's Big AI Flub
McDonald's hiring platform was using its original default credentials and inadvertently exposed information belonging to approximately 64 million job applicants.

15 Jul 2025
Biztonsági szemle
AI Is Reshaping How Attorneys Practice Law
Experts recommend enhanced AI literacy, training around the ethics of using AI, and verification protocols to maintain credibility in an increasingly AI-influenced courtroom.

15 Jul 2025
Biztonsági szemle
AsyncRAT Spawns Concerning Labyrinth of Forks
Since surfacing on GitHub in 2019, AsyncRAT has become a poster child for how open source malware can democratize cybercrime, with a mazelike footprint of variants available across the spectrum of functionality.
Pagination
- Previous page ‹‹
- Page 116
- Next page ››