Security Bulletin

23 Jun 2025
Biztonsági szemle
ISC Stormcast For Monday, June 23rd, 2025 https://isc.sans.edu/podcastdetail/9500, (Mon, Jun 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
21 Jun 2025
Biztonsági szemle
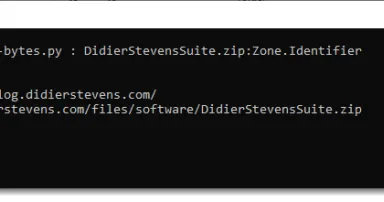
ADS & Python Tools, (Sat, Jun 21st)
Ehsaan Mavani talks about Alternate Data Streams (ADS) in diary entry " Alternate Data Streams ? Adversary Defense Evasion and Detection [Guest Diary]".

21 Jun 2025
Biztonsági szemle
AWS Enhances Cloud Security With Better Visibility Features
At this week's re:Inforce 2025 conference, the cloud giant introduced new capabilities to several core security products to provide customers with better visibility and more context on potential threats.

21 Jun 2025
Biztonsági szemle
Jira tickets become attack vectors in PoC ‘living off AI’ attack
Cato Networks’ prompt injection exploit highlights the risks of external input to internal AI services.

20 Jun 2025
Biztonsági szemle
Donut Holes, clickfix, rapperbots, bad devs, war, Doug Rants about Backups, and More. - SWN #487

20 Jun 2025
Biztonsági szemle
Hackers Post Dozens of Malicious Copycat Repos to GitHub
As package registries find better ways to combat cyberattacks, threat actors are finding other methods for spreading their malware to developers.
20 Jun 2025
Biztonsági szemle
AI isn’t ready to go solo: Expert urges collaborative security strategy
Relying solely on AI for identity security overlooks essential human capabilities such as adaptability, creativity, and nuanced judgment.

20 Jun 2025
Biztonsági szemle
Aflac among victims in cyberattacks targeting US insurance industry
Aflac incident comes four days after Google warned that Scattered Spider was attacking the U.S. insurance industry.

20 Jun 2025
Biztonsági szemle
Telecom Giant Viasat Is Latest Salt Typhoon Victim
The communications company shared the discoveries of its investigation with government partners, but there is little information they can publicly disclose other than that there seems to be no impact on customers.

20 Jun 2025
Biztonsági szemle
How Cyber Warfare Changes the Face of Geopolitical Conflict
As geopolitical tensions rise, the use of cyber operations and hacktivists continues to grow, with the current conflict between Israel and Iran showing the new face of cyber-augmented war.

20 Jun 2025
Biztonsági szemle
How to Lock Down the No-Code Supply Chain Attack Surface
Securing the no-code supply chain isn't just about mitigating risks — it's about enabling the business to innovate with confidence.

20 Jun 2025
Biztonsági szemle
Passkeys on Facebook, Messenger for mobile imminent
Meta has revealed plans to roll out passkeys for Facebook on Android and iOS soon, as well as for Messenger in the coming months, in a bid to bolster user account security, The Hacker News reports.
Pagination
- Previous page ‹‹
- Page 145
- Next page ››