Security Bulletin

21 Jan 2026
Biztonsági szemle
Cisco URWB: Powering Industrial AI & Automation on the Factory Floor
Discover how Cisco URWB powers industrial AI & automation for companies like E80 & Planet Farms, offering wireless reliability and operational simplicity.

21 Jan 2026
Biztonsági szemle
Complex VoidLink Linux Malware Created by AI
Researchers say the advanced framework was built almost entirely by agents, marking a significant evolution in the use of AI to develop wholly original malware.

21 Jan 2026
Biztonsági szemle
'Damn Vulnerable' Training Apps Leave Vendors' Clouds Exposed
Hackers are already leveraging these over-permissioned programs to access the IT systems of major security vendors.

21 Jan 2026
Biztonsági szemle
CVE-2025-13878: Malformed BRID/HHIT records can cause named to terminate unexpectedly
CVE: CVE-2025-13878 Title: Malformed BRID/HHIT records can cause named to terminate unexpectedly Document version: 2.0 Posting date: 21 January 2026 Program impacted: BIND 9 Versions affected: BIND 9.18.40 -> 9.18.43 9.20.13 -> 9.20.17 9.21.12 -> 9...
21 Jan 2026
Biztonsági szemle
Join Cisco at the Rocky Mountain Cyberspace Symposium to unlock new possibilities for intelligent networks!
Join Cisco at the Rocky Mountain Cyberspace Symposium 2026 to experience hands-on AI, automation, and security innovations—plus live demos, expert sessions, and engaging activities designed to unlock your network’s full potential.
21 Jan 2026
Biztonsági szemle
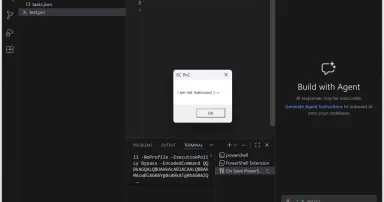
Automatic Script Execution In Visual Studio Code, (Wed, Jan 21st)
Visual Studio Code is a popular open-source code editor[ 1]. But it's much more than a simple editor, it's a complete development platform that supports many languages and it is available on multiple platforms. Used by developers worldwide...

21 Jan 2026
Biztonsági szemle
ISC Stormcast For Wednesday, January 21st, 2026 https://isc.sans.edu/podcastdetail/9774, (Wed, Jan 21st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

20 Jan 2026
Biztonsági szemle
'CrashFix' Scam Crashes Browsers, Delivers Malware
The attack consists of a NexShield malicious browser extension, a social engineering technique to crash the browser, and a Python-based RAT.

20 Jan 2026
Biztonsági szemle
Mass Spam Attacks Leverage Zendesk Instances
The CRM vendor advised ignoring or deleting suspicious emails and said the attacks were not tied to any breach or software vulnerability.

20 Jan 2026
Biztonsági szemle
Accelerating Ethernet-Native AI Clusters with Intel® Gaudi® 3 AI Accelerators and Cisco Nexus 9000
Cisco Nexus 9300 800G switches and Intel® Gaudi® 3 AI accelerators combine to deliver a scalable, high-performance, and open solution for enterprise AI workloads. This integrated architecture enables organizations to build robust AI infrastructure...

20 Jan 2026
Biztonsági szemle
Vulnerabilities Threaten to Break Chainlit AI Framework
Familiar bugs in a popular open source framework for AI chatbots could give attackers dangerous powers in the cloud.

20 Jan 2026
Biztonsági szemle
Celebrating Innovation: Announcing the Finalists for the Cisco Customer Achievement Awards: EMEA 2026!
Cisco is thrilled to announce finalists for the Cisco Customer Achievement Awards 2026 in the EMEA region! These awards celebrate and honor the remarkable achievements of our customers—organizations that are redefining what’s possible through...
Pagination
- Previous page ‹‹
- Page 16
- Next page ››