Security Bulletin
19 May 2025
Biztonsági szemle
RAT Dropped By Two Layers of AutoIT Code, (Mon, May 19th)
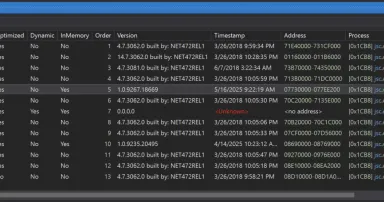
Like .Net, AutoIT[ 1] remains a popular language for years in the malware ecosystem. It's a simple language that can interact with all the components of the Windows operating system. I regularly discover AutoIT3 binaries...

19 May 2025
Biztonsági szemle
ISC Stormcast For Monday, May 19th, 2025 https://isc.sans.edu/podcastdetail/9456, (Mon, May 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
17 May 2025
Biztonsági szemle
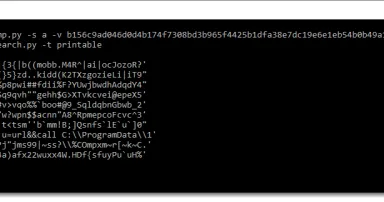
xorsearch.py: Python Functions, (Sat, May 17th)
A couple years ago I published tool xorsearch.py for this diary entry: " Small Challenge: A Simple Word Maldoc - Part 4".

16 May 2025
Biztonsági szemle
Steganography, RICO, CMMC, End of 10, AI is coming for you, Aaran Leyland and More... - SWN #477

16 May 2025
Biztonsági szemle
Google Chrome data leakage bug confirmed as actively exploited
Insufficient policy enforcement could lead to data disclosure when loading malicious resources.
16 May 2025
Biztonsági szemle
Explore Cisco IOS XE Automation at Cisco Live US 2025
Cisco IOS XE offers advanced programmability and automation capabilities that simplify network management and reduce complexity. By utilizing open, standards-based APIs such as NETCONF, RESTCONF, and… Read more on Cisco Blogs

16 May 2025
Biztonsági szemle
Coinbase Extorted, Offers $20M for Info on Its Hackers
Coinbase is going Liam Neeson on its attackers, potentially setting a new precedent for incident response in the wake of crypto- and blockchain-targeting cyberattacks.

16 May 2025
Biztonsági szemle
Australian Human Rights Commission Leaks Docs in Data Breach
An internal error led to public disclosure of reams of sensitive data that could be co-opted for follow-on cyberattacks.

16 May 2025
Biztonsági szemle
Dynamic DNS Emerges as Go-to Cyberattack Facilitator
Scattered Spider and other phishers and hacking groups are using rentable subdomains from dynamic DNS providers to obfuscate their activity and impersonate well-known brands.

16 May 2025
Biztonsági szemle
Attacker Specialization Puts Threat Modeling on Defensive
Specialization among threat groups poses challenges for defenders, who now must distinguish between different actors responsible for different facets of an attack.

16 May 2025
Biztonsági szemle
Sednit group's 'Operation RoundPress' targets webmail servers globally
While most of the victims are based overseas, security pros say it’s plausible the group will also target North America.

16 May 2025
Biztonsági szemle
The Future is Coming Faster than You Think
At Cisco, we are building the core infrastructure of the AI era. As new solutions like Codex exemplify, the future of AI will be agentic. We envision a future where billions of AI agents are working together harmoniously on our behalf.
Pagination
- Previous page ‹‹
- Page 205
- Next page ››