Security Bulletin

23 Apr 2025
Biztonsági szemle
Verizon: Edge Bugs Soar, Ransoms Lag, SMBs Bedeviled
The cybersecurity landscape confounded expectations in 2024, as anticipated threats and risk didn't materialize and less widely touted attack scenarios shot up.

23 Apr 2025
Biztonsági szemle
ISC Stormcast For Wednesday, April 23rd, 2025 https://isc.sans.edu/podcastdetail/9420, (Wed, Apr 23rd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
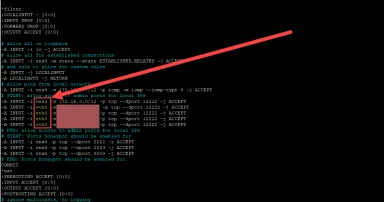
23 Apr 2025
Biztonsági szemle
Honeypot Iptables Maintenance and DShield-SIEM Logging, (Wed, Apr 23rd)
In the last week I ran into some issues that I hadn't anticipated:

22 Apr 2025
Biztonsági szemle
How Emerging AI Frameworks Drive Business Value and Mitigate Risk
Understanding how multiple AI models speak to each other and deciding which framework to use requires careful evaluation of both the business benefits of advanced AI orchestration and the cybersecurity implications of connecting automated services.

22 Apr 2025
Biztonsági szemle
Google fixes Cloud Composer privilege escalation vulnerability
Tenable researchers say “ConfusedComposer” highlights how attackers can exploit cloud service permissions.

22 Apr 2025
Biztonsági szemle
Microsoft Purges Millions of Cloud Tenants in Wake of Storm-0558
The tech giant is boosting Entra ID and MSA security as part of the wide-ranging Secure Future Initiative (SFI) that the company launched following a Chinese APT's breach of its Exchange Online environment in 2023.

22 Apr 2025
Biztonsági szemle
Brains, Elusive Comet, AI Scams, Microsoft Dog Food, Deleting Yourself, Josh Marpet - SWN #470

22 Apr 2025
Biztonsági szemle
City of Abilene Goes Offline in Wake of Cyberattack
The Texas municipality is following its incident response playbook as it works with a third-party to investigate the scope and scale of the attack.

22 Apr 2025
Biztonsági szemle
3 More Healthcare Orgs Hit by Ransomware Attacks
Dialysis firm DaVita, Wisconsin-based Bell Ambulance, and Alabama Ophthalmology Associates all suffered apparent or confirmed ransomware attacks this month.

22 Apr 2025
Biztonsági szemle
Two senior officials resign from federal cybersecurity office, CISA
Continued brain drain includes two of the experts who managed CISA’s Secure by Design program.

22 Apr 2025
Biztonsági szemle
'Cookie Bite' Entra ID Attack Exposes Microsoft 365
A proof-of-concept (PoC) attack vector exploits two Azure authentication tokens from within a browser, giving threat actors persistent access to key cloud services, including Microsoft 365 applications.

22 Apr 2025
Biztonsági szemle
Terra Security Automates Penetration Testing With Agentic AI
Agentic AI's appeal is growing as organizations seek more autonomous and hands-off approaches to their security protocols.
Pagination
- Previous page ‹‹
- Page 252
- Next page ››