Security Bulletin

25 Mar 2025
Biztonsági szemle
Chinese hackers spend years roaming telecommunications service
China Chopper malware allowed threat group "Weaver Ant" to remain undetected for years.

25 Mar 2025
Biztonsági szemle
Security Tech That Can Make a Difference During an Attack
The recent report of how Volt Typhoon compromised systems at a water utility highlight security technologies and processes that helped detect the compromise and clean up the network.

25 Mar 2025
Biztonsági szemle
Security Tech That Can Make a Difference During an Attack
The recent report of how Volt Typhoon compromised systems at a water utility highlight security technologies and processes that helped detect the compromise and clean up the network.

25 Mar 2025
Biztonsági szemle
Curdled Miscreant, VanHelsing, MFA, Room 237, MFA, Velora, 23nMe, Josh Marpet... - SWN #462

25 Mar 2025
Biztonsági szemle
OPSEC Nightmare: Leaking US Military Plans to a Reporter
Experts say the leakage of US military plans to a reporter this month reflects a severe operational security failure on the part of US leadership.

25 Mar 2025
Biztonsági szemle
South African Poultry Company Reports $1M Loss After Cyber Intrusion
The company reports that no sensitive information was breached or stolen in the cyber intrusion and that its operations are running normally again.

25 Mar 2025
Biztonsági szemle
Fate of DNA data raises privacy, identity issues in 23andMe bankruptcy
Privacy advocates worry how the DNA data will be managed during company's Chapter 11 proceedings.

25 Mar 2025
Biztonsági szemle
Accused Snowflake Attacker 'Judische' Agrees to US Extradition
Though there is no confirmation as to when this extradition will occur, Alexander Moucka agreed to be transferred in writing before a judge.

25 Mar 2025
Biztonsági szemle
AI has become the supply chain
AI no longer just assists with software development – it’s the supply chain – which means teams must secure AI like their entire software ecosystem.
25 Mar 2025
Biztonsági szemle
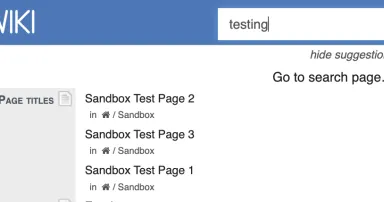
X-Wiki Search Vulnerability exploit attempts (CVE-2024-3721), (Tue, Mar 25th)
Creating a secure Wiki is hard. The purpose of a wiki is to allow "random" users to edit web pages. A good Wiki provides users with great flexibility, but with great flexibility comes an even "greater" attack surface. File uploads and markup (or...
25 Mar 2025
Biztonsági szemle
Marketing Velocity (MV) Reimagined Welcomes Learning: The One MV Story
Cisco's Marketing Velocity unifies learning and campaigns, enabling partner marketers with tools and strategies for seamless alignment, enhanced demand generation, and improved business outcomes—all within a single platform.

25 Mar 2025
Biztonsági szemle
Delivering Resilient Connectivity for AI
Preparing for the AI era - Cisco is here with the technologies that will help hyperscalers and service providers navigate the journey.
Pagination
- Previous page ‹‹
- Page 280
- Next page ››