Security Bulletin

12 Feb 2025
Biztonsági szemle
Game On: Embark on a New Hacking Mission in Cisco U.
It’s time to bring in the new with our next ethical hacking Capture the Flag challenge in Cisco U., Pentest Quest - Nmap & Kali.

12 Feb 2025
Biztonsági szemle
The blueprint for cyber resilience: How businesses can adapt and thrive
LevelBlue's Theresa Lanowitz discusses what cyber resilience is and the path to get there.

12 Feb 2025
Biztonsági szemle
Is AI a Friend or Foe of Healthcare Security?
When it comes to keeping patient information safe, people empowerment is just as necessary as deploying new technologies.
12 Feb 2025
Biztonsági szemle
CISA Adds Two Known Exploited Vulnerabilities to Catalog
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2025-24200 Apple iOS and iPadOS Incorrect Authorization Vulnerability CVE-2024-41710 Mitel SIP Phones Argument...
12 Feb 2025
Biztonsági szemle
CISA and FBI Warn of Malicious Cyber Actors Using Buffer Overflow Vulnerabilities to Compromise Software
CISA and the Federal Bureau of Investigation (FBI) have released a Secure by Design Alert, Eliminating Buffer Overflow Vulnerabilities, as part of their cooperative Secure by Design Alert series—an ongoing series aimed at advancing industry-wide best...

12 Feb 2025
Biztonsági szemle
Cisco and Wiz Collaborate to Enhance Cloud Security: Tackling AI-Generating Threats in Complex IT Infrastructures
Cisco is collaborating with Wiz. Together, they aim to improve cloud security for enterprises grappling with AI-generated threats in intricate IT landscapes.

12 Feb 2025
Biztonsági szemle
Achieve Transformative Network Security With Cisco Hybrid Mesh Firewall
Hybrid Mesh Firewall addresses 3 forces: Fine-grained composition & distribution of apps in data centers, complex modern networks & sophisticated threats.
12 Feb 2025
Biztonsági szemle
India's Cybercrime Problems Grow as Nation Digitizes
More than half of attacks on Indian businesses come from outside the country, while 45% of those targeting consumers come from Cambodia, Myanmar, and Laos.
12 Feb 2025
Biztonsági szemle
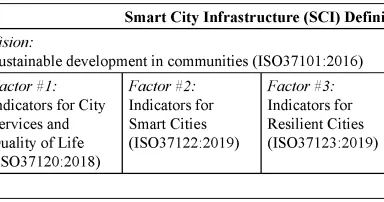
An ontology for threats, cybercrime and digital forensic investigation on Smart City Infrastructure, (Wed, Feb 12th)
Blue teams have it hard â they maintain a watchful eye on whatever technology is deployed to detect threats, respond to incidents, perform digital forensics and reverse malware (or make malware happy!) when needed. Hopefully, no one has to handle...

12 Feb 2025
Biztonsági szemle
ISC Stormcast For Wednesday, February 12th, 2025 https://isc.sans.edu/podcastdetail/9320, (Wed, Feb 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

12 Feb 2025
Biztonsági szemle
LockBit crackdown continues with Zservers sanctions
The Russia-based bulletproof hosting service provided infrastructure to LockBit affiliates, officials say.

12 Feb 2025
Biztonsági szemle
Gartner: Most Security Leaders Cannot Balance Data Security, Business Goals
The analyst firm recommends defining security and governance processes while reducing friction for business stakeholders.
Pagination
- Previous page ‹‹
- Page 352
- Next page ››