Security Bulletin
7 Feb 2025
Biztonsági szemle
Trimble Releases Security Updates to Address a Vulnerability in Cityworks Software
CISA is collaborating with private industry partners to respond to reports of exploitation of a vulnerability (CVE-2025-0994) discovered by Trimble impacting its Cityworks Server AMS (Asset Management System). Trimble has released security updates...
7 Feb 2025
Biztonsági szemle
CISA Adds One Known Exploited Vulnerability to Catalog
CISA has added one vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2025-0994 Trimble Cityworks Deserialization Vulnerability These types of vulnerabilities are frequent attack vectors for...

7 Feb 2025
Biztonsági szemle
Sajtószemle – 2025. 6. hét
A 2025. 6. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2025.01.31. és 2025.02.06. között kezelt incidensek statisztikai adatait is tartalmazza.
7 Feb 2025
Biztonsági szemle
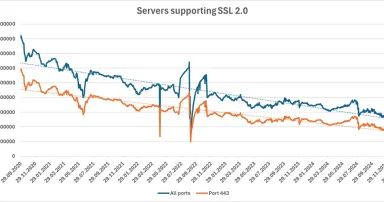
SSL 2.0 turns 30 this Sunday... Perhaps the time has come to let it die?, (Fri, Feb 7th)
The SSL 2.0 protocol was originally published back in February of 1995[ 1], and although it was quickly found to have significant security weaknesses, and a more secure alternative was released only a year later[ 2], it still received a fairly wide...

7 Feb 2025
Biztonsági szemle
ISC Stormcast For Friday, February 7th, 2025 https://isc.sans.edu/podcastdetail/9314, (Fri, Feb 7th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

7 Feb 2025
Biztonsági szemle
Cybercrime Forces Local Law Enforcement to Shift Focus
Local law enforcements need to steer away from "place-based policing" when investigating cybercrimes.

6 Feb 2025
Biztonsági szemle
Kimsuky shifts tactics from traditional backdoors to RDP, proxies
The North Korean APT group has leveraged a custom RDP Wrapper and new malware called forceCopy in recent campaigns.

6 Feb 2025
Biztonsági szemle
Former Google engineer charged with stealing AI trade secrets
A Chinese national is facing multiple charges of economic espionage and theft of trade secrets after he was accused of stealing AI technology from Google

6 Feb 2025
Biztonsági szemle
7AI Streamlines Security Operations With Autonomous AI Agents
Cybereason co-founders launch their second act with a security startup focused on offering a platform that uses agentic AI to offload repetitive tasks commonly performed by security analysts.

6 Feb 2025
Biztonsági szemle
Researcher Outsmarts, Jailbreaks OpenAI's New o3-mini
OpenAI's latest tech can reason better than its previous models could, but not well enough to ferret out careful social engineering.

6 Feb 2025
Biztonsági szemle
US Cybersecurity Efforts for Spacecraft Are Up in the Air
While President Trump supported federal space efforts during his first administration, the addition of SpaceX chief Elon Musk to his circle likely means challenges for regulating spacecraft cybersecurity, experts say.
Pagination
- Previous page ‹‹
- Page 359
- Next page ››