Security Bulletin
6 Feb 2025
Biztonsági szemle
Schneider Electric EcoStruxure
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.5 ATTENTION: Low attack complexity Vendor: Schneider Electric Equipment: EcoStruxure Vulnerability: Uncontrolled Search Path Element 2. RISK EVALUATION Successful exploitation of this vulnerability allows for...
6 Feb 2025
Biztonsági szemle
Orthanc Server
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.2 ATTENTION: Exploitable remotely/low attack complexity Vendor: Orthanc Equipment: Orthanc Server Vulnerability: Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of this...

6 Feb 2025
Biztonsági szemle
The Unbreakable Multi-Layer Anti-Debugging System, (Thu, Feb 6th)
The title of this diary is based on the string I found in a malicious Python script that implements many anti-debugging techniques. If some were common, others were interesting and demonstrated how low-level high-level languages like Python can...

6 Feb 2025
Biztonsági szemle
Basket of Bank Trojans Defraud Citizens of East India
Cheap banking scams are often easier to pull off in a country with older devices, fewer regulations, and experienced fraudsters.

6 Feb 2025
Biztonsági szemle
ISC Stormcast For Thursday, February 6th, 2025 https://isc.sans.edu/podcastdetail/9312, (Thu, Feb 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

5 Feb 2025
Biztonsági szemle
Ransomware payments drop 35% in 2024, first decrease since 2022
The first half of 2024 recorded an increase in ransomware payouts.
5 Feb 2025
Biztonsági szemle
C-Suite Cybersecurity Responsibilities, Humble Leaders, and Effective Communication - BSW #381

5 Feb 2025
Biztonsági szemle
Veeam Updater receives update for critical RCE flaw
The vulnerability affects Veeam Backup for Salesforce, AWS, Microsoft Azure, Google Cloud and more.

5 Feb 2025
Biztonsági szemle
Infostealers targeting macOS jumped by 101% in second half of 2024
While infostealers are often seen as less dangerous compared with trojans, they can exfiltrate sensitive data, leading to data breaches.
5 Feb 2025
Biztonsági szemle
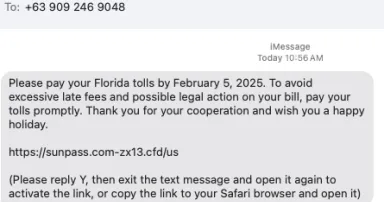
Phishing via "com-" prefix domains, (Wed, Feb 5th)
Phishing is always a "whack the mole" like game. Attackers come up with new ways to fool victims. Security tools are often a step behind. Messages claiming to collect unpaid tolls are one current common theme among phishing (smishing?) messages. I...

5 Feb 2025
Biztonsági szemle
Abandoned AWS Cloud Storage: A Major Cyberattack Vector
New research highlights how bad actors could abuse deleted AWS S3 buckets to create all sorts of mayhem, including a SolarWinds-style supply chain attack.

5 Feb 2025
Biztonsági szemle
Build a vulnerability management program with internet exposure in mind
Teams need to adapt their vulnerability management programs to the reality that most of their business today runs on the internet.
Pagination
- Previous page ‹‹
- Page 362
- Next page ››