Security Bulletin

29 Oct 2025
Biztonsági szemle
Dentsu Subsidiary Breached, Employee Data Stolen
A subsidiary of Japanese marketing and PR giant Dentsu lost sensitive data to unidentified threat actors, the parent company said.

29 Oct 2025
Biztonsági szemle
Microsoft Security Change for Azure VMs Creates Pitfalls
Firms using Azure infrastructure gained a reprieve from a security-focused switch that could have broken apps that relied on public Internet access.

29 Oct 2025
Biztonsági szemle
Botnets Step Up Cloud Attacks Via Flaws, Misconfigurations
Infamous botnets like Mirai are exploiting Web-exposed assets such as PHP servers, IoT devices, and cloud gateways to gain control over systems and build strength.

29 Oct 2025
Biztonsági szemle
Build Toward What’s Next with Cisco Marketplace
Cisco Marketplace helps IT teams modernize operations with curated integrations to automate tasks, cut alert noise, and connect workflows. Start now.

29 Oct 2025
Biztonsági szemle
From Power Users to Protective Stewards: How to Tune Security Training for Specialized Employees
The best security training programs build strong security culture by focusing on high-risk groups, including developers, executives, and finance pros.

29 Oct 2025
Biztonsági szemle
SE Labs Names Cisco Secure Firewall Best Enterprise NGFW 2025
Cisco Secure Firewall wins SE Labs’ 2025 Best NGFW award — the first ever to earn dual AAA ratings for both protection and performance. Zero breaches, Zero compromises.

29 Oct 2025
Biztonsági szemle
CVE-2025-11232: Invalid characters cause assert
CVE: CVE-2025-11232 Title: Invalid characters cause assert Document version: 2.0 Posting date: 29 October 2025 Program impacted: Kea Versions affected: Kea 3.0.1 -> 3.0.1 3.1.1 -> 3.1.2 Versions NOT affected: Kea 2.6.0 -> 2.6.4 2.7.0 -> 2.7.9 3.0.0 -...

29 Oct 2025
Biztonsági szemle
Cyber resilience for all: How Cisco and NIIT Foundation are securing India’s digital future
As India's digital transformation accelerates, Cisco and NIIT Foundation are meeting the moment with Cyber Suraksha — training over one million people in cybersecurity while creating pathways to opportunity and building a safer, more digitally...

29 Oct 2025
Biztonsági szemle
Cybersecurity Firms See Surge in AI-Powered Attacks Across Africa
Africa becomes a proving ground for AI-driven phishing, deepfakes, and impersonation, with attackers testing techniques against governments and enterprises.
29 Oct 2025
Biztonsági szemle
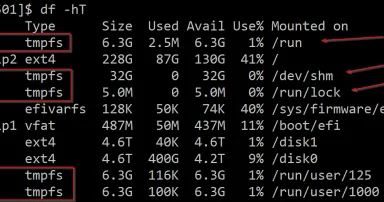
How to collect memory-only filesystems on Linux systems, (Wed, Oct 29th)
I've been doing Unix/Linux IR and Forensics for a long time. I logged into a Unix system for the first time in 1983. That's one of the reasons I love teaching FOR577[1], because I have stories that go back to before some of my...

29 Oct 2025
Biztonsági szemle
ISC Stormcast For Wednesday, October 29th, 2025 https://isc.sans.edu/podcastdetail/9676, (Wed, Oct 29th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

29 Oct 2025
Biztonsági szemle
AI-Generated Code Poses Security, Bloat Challenges
Development teams that fail to create processes around AI-generated code face more technical and security debt, as vulnerabilities get replicated.
Pagination
- Previous page ‹‹
- Page 39
- Next page ››