Security Bulletin
20 Oct 2025
Biztonsági szemle
Using Syscall() for Obfuscation/Fileless Activity, (Mon, Oct 20th)
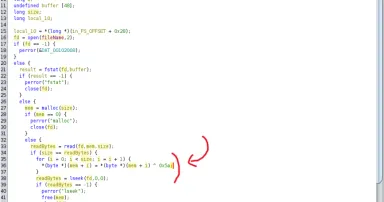
I found another piece of malware this weekend. This one looks more like a proof-of-concept because the second-stage payload is really "simple", but it attracted my attention because it uses a nice technique to obfuscate the code.

19 Oct 2025
Biztonsági szemle
ISC Stormcast For Monday, October 20th, 2025 https://isc.sans.edu/podcastdetail/9662, (Sun, Oct 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

18 Oct 2025
Biztonsági szemle
Cyber Academy Founder Champions Digital Safety for All
Aliyu Ibrahim Usman, founder of the Cyber Cadet Academy in Nigeria, shares his passion for raising cybersecurity awareness in the wake of mounting security concerns worldwide.

17 Oct 2025
Biztonsági szemle
Microsoft Disrupts Ransomware Campaign Abusing Azure Certificates
Microsoft revoked more than 200 digital certificates that threat actors used to sign fake Teams binaries that set the stage for Rhysida ransomware attacks.

17 Oct 2025
Biztonsági szemle
AI Agent Security: Whose Responsibility Is It?
The shared responsibility model of data security, familiar from cloud deployments, is key to agentic services, but cybersecurity teams and corporate users often struggle with awareness and managing that risk.

17 Oct 2025
Biztonsági szemle
AI Chat Data Is History's Most Thorough Record of Enterprise Secrets. Secure It Wisely
AI interactions are becoming one of the most revealing records of human thinking, and we're only beginning to understand what that means for law enforcement, accountability, and privacy.

17 Oct 2025
Biztonsági szemle
Mastering the Course of Wireless Transformation with Cisco and USGA
Read how Cisco powered the 125th U.S. Open with Wi-Fi 7, 550 access points, and a cloud-managed gateway for seamless, scalable connectivity and enhanced fan experiences.

17 Oct 2025
Biztonsági szemle
Sajtószemle – 2025. 42. hét
Megjelent a 2025. 42. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2025.10.10. és 2025.10.16. között kezelt incidensek, valamint az elosztott kormányzati IT biztonsági csapdarendszerből (GovProbe1) származó adatok statisztikai eloszlását is...

17 Oct 2025
Biztonsági szemle
TikTok Videos Promoting Malware Installation, (Fri, Oct 17th)
Attackers are everywhere! They try to abuse victims using new communication channels and social engineering techniques! Somebody pointed my to the following Tik-Tok video: hxxps://vm[.]tiktok[.]com/ZGdaCkbEF/.

17 Oct 2025
Biztonsági szemle
ISC Stormcast For Friday, October 17th, 2025 https://isc.sans.edu/podcastdetail/9660, (Fri, Oct 17th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

16 Oct 2025
Biztonsági szemle
Cyberattackers Target LastPass, Top Password Managers
Be aware: a rash of phishing campaigns are leveraging the anxiety and trust employees have in password vaults securing all of their credentials.

16 Oct 2025
Biztonsági szemle
Leaks in Microsoft VS Code Marketplace Put Supply Chain at Risk
Researchers discovered more than 550 unique secrets exposed in Visual Studio Code marketplaces, prompting Microsoft to bolster security measures.
Pagination
- Previous page ‹‹
- Page 46
- Next page ››