Security Bulletin

10 Oct 2025
Biztonsági szemle
Commentary Section Launches New, More Opinionated Era
Dark Reading is looking for leading industry experts with a point of view they want to share with the rest of the cybersecurity community for our new Commentary section.

10 Oct 2025
Biztonsági szemle
Sajtószemle – 2025. 41. hét
Megjelent a 2025. 41. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2025.10.03. és 2025.10.09. között kezelt incidensek, valamint az elosztott kormányzati IT biztonsági csapdarendszerből (GovProbe1) származó adatok statisztikai eloszlását is...

10 Oct 2025
Biztonsági szemle
ISC Stormcast For Friday, October 10th, 2025 https://isc.sans.edu/podcastdetail/9650, (Fri, Oct 10th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

9 Oct 2025
Biztonsági szemle
GitHub Copilot 'CamoLeak' AI Attack Exfiltrates Data
While GitHub has advanced protections for its built-in AI agent, a researcher came up with a creative proof-of-concept (PoC) attack for exfiltrating code and secrets via Copilot.

9 Oct 2025
Biztonsági szemle
SonicWall: 100% of Firewall Backups Possibly Breached
SonicWall said a breach it disclosed last month affected firewall configuration files for all customers who have used SonicWall’s cloud backup service — up from its previous 5% estimate.

9 Oct 2025
Biztonsági szemle
Fastly CISO: Using Major Incidents as Career Catalysts
Marshall Erwin shares how crisis leadership shaped his path from CIA analyst to the US Congress to protecting global Web traffic at Fastly.
9 Oct 2025
Biztonsági szemle
Your Computing Future Is at the Edge: Are You Ready for AI’s New Frontier?
Central to AI transformation is an edge infrastructure that helps drive innovation. Learn how a unified edge strategy unleashes the full power of data and computing for AI.

9 Oct 2025
Biztonsági szemle
Take Note: Cyber-Risks With AI Notetakers
Transcription applications are joining your online meetings. Here's how to create policies for ensuring compliance and security of your information.

9 Oct 2025
Biztonsági szemle
Empowering Rural Healthcare: How Cisco and HCF Drive Digital Transformation
Unlock the full potential of rural healthcare—discover how the Rural Healthcare Connect Fund, paired with Cisco’s innovative solutions, empowers providers to modernize their networks, enhance patient care, and overcome unique rural challenges.

9 Oct 2025
Biztonsági szemle
SVS Engineers: Who are the people that test-drive your network?
Cisco Solution Validation Services (SVS) engineers design tailored test blueprints, validate complex network deployments in labs, and deliver future-proof, reliable solutions.

9 Oct 2025
Biztonsági szemle
Chaos Ransomware Upgrades with Aggressive New C++ Variant
New encryption, wiper, and cryptocurrency-stealing capabilities make the evolving ransomware-as-a-service operation more dangerous than ever.
9 Oct 2025
Biztonsági szemle
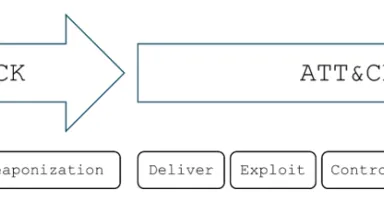
[Guest Diary] Building Better Defenses: RedTail Observations from a Honeypot, (Thu, Oct 9th)
[This is a Guest Diary by Jin Quan Low, an ISC intern as part of the SANS.edu Bachelor's Degree in Applied Cybersecurity (BACS) program [1].]
Pagination
- Previous page ‹‹
- Page 49
- Next page ››