Security Bulletin
8 Aug 2024
Biztonsági szemle
CISA Releases One Industrial Control Systems Advisory
CISA released one Industrial Control Systems (ICS) advisory on August 8, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-24-221-01 Dorsett Controls InfoScan CISA...
8 Aug 2024
Biztonsági szemle
Best Practices for Cisco Device Configuration
In recent incidents, CISA has seen malicious cyber actors acquire system configuration files by leveraging available protocols or software on devices, such as abusing the legacy Cisco Smart Install feature. CISA recommends organizations disable Smart...

8 Aug 2024
Biztonsági szemle
ISC Stormcast For Thursday, August 8th, 2024 https://isc.sans.edu/podcastdetail/9088, (Thu, Aug 8th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

8 Aug 2024
Biztonsági szemle
Ransomware gangs: How low will they go?
Ransomware operators are increasingly turning to new, and in some cases extremely concerning, tactics to extort payments from victims.

8 Aug 2024
Biztonsági szemle
Amid the glitter of Las Vegas, don’t forget the cybersecurity basics
The latest AI-enabled tools are enticing, but don’t lose focus on what’s really important as the show continues on.

8 Aug 2024
Biztonsági szemle
Black Hat USA: Wi-Fi tracking flaw puts the ‘BS’ in BSSID
Geolocation services for a number of popular mobile hardware vendors can be used to perform widescale Wi-Fi network monitoring.

8 Aug 2024
Biztonsági szemle
Hazy Issue in Entra ID Allows Privileged Users to Become Global Admins
Invisible authentication mechanisms in Microsoft allow any attacker to escalate from privileged to super-duper privileged in cloud environments, paving the way for complete takeover.
8 Aug 2024
Biztonsági szemle
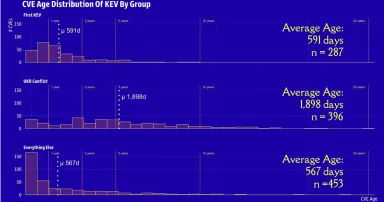
Monitoring Changes in KEV List Can Guide Security Teams
The number of additions to the Known Exploited Vulnerabilities catalog is growing quickly, but even silent changes to already-documented flaws can help security teams prioritize.

7 Aug 2024
Biztonsági szemle
From Cybersecurity Practitioner to Advocacy: My Journey Back to Cisco
Discover Kyle Winters' journey from cybersecurity practitioner to Cisco technical advocate. Learn about his experiences, upcoming tutorials, and how to engage with the community.

7 Aug 2024
Biztonsági szemle
CrowdStrike Will Give Customers Control Over Falcon Sensor Updates
The security vendor has also implemented several changes to protect against the kind of snafu that crashed 8.5 million Windows computers worldwide last month.

7 Aug 2024
Biztonsági szemle
RISC-V business: 'GhostWrite' chip flaw detailed at Black Hat USA
The RISC-V platform has found itself presented with a new security flaw based within the hardware of some CPUs.

7 Aug 2024
Biztonsági szemle
Knostic Wins 2024 Black Hat Startup Spotlight Competition
During a "Shark Tank"-like final, each startup's representative spent five minutes detailing their company and product, with an additional five minutes to take questions from eight judges from Omdia, investment firms, and top companies in cyber.
Pagination
- Previous page ‹‹
- Page 679
- Next page ››