Security Bulletin

2 Jan 2024
Biztonsági szemle
Novel JinxLoader malware loader emerges
Phishing attacks using the novel JinxLoader malware loader have been launched to facilitate the deployment of the Formbook and XLoader payloads, reports The Hacker News.

2 Jan 2024
Biztonsági szemle
Israeli orgs subjected to suspected Iranian hacking attacks
Suspected Iranian state-backed hacking group Cyber Toufan has taken credit for compromising dozens of organizations across Israel in late November amid the ongoing Israel-Hamas war, according to The Record, a news site by cybersecurity firm Recorded...
2 Jan 2024
Biztonsági szemle
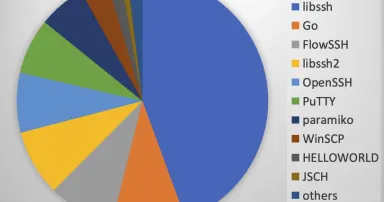
Fingerprinting SSH Identification Strings, (Tue, Jan 2nd)
For HTTP, logging and fingerprinting browser user agents is standard practice. Many anti-automation tricks use the user agent and compare it to other browser artifacts, for example, supported JavaScript APIs, to detect bots. SSH offers an...

2 Jan 2024
Biztonsági szemle
Israel Battles Spike in Wartime Hacktivist, OT Cyberattacks
Israel's cybersecurity industry made strides in the past year despite the backdrop of the war in Gaza.
2 Jan 2024
Biztonsági szemle
CISO Planning for 2024 May Struggle When It Comes to AI
Artificial intelligence (AI) is constantly evolving. How can security executives plan for something so unpredictable?

2 Jan 2024
Biztonsági szemle
Localization Mandates, AI Regs to Pose Major Data Challenges in 2024
With more than three-quarters of countries adopting some form of data localization and, soon, three-quarters of people worldwide protected by privacy rules, companies need to take care.

2 Jan 2024
Biztonsági szemle
Attackers Abuse Google OAuth Endpoint to Hijack User Sessions
Infostealers such as Lumma and Rhadamanthys have integrated the generation of persistent Google cookies through token manipulation.

2 Jan 2024
Biztonsági szemle
Startups Scramble to Build Immediate AI Security
AI may be inherently insecure, but only a handful of startups have put forward real visions to mitigate AI's threats and keep data private.

2 Jan 2024
Biztonsági szemle
Biggest AI trends of 2024: According to top security experts
Cybersecurity prognosticators share predictions for artificial intelligence's uses, abuses and surprising impact on businesses risks in the year ahead.

2 Jan 2024
Biztonsági szemle
10 Years After Yahoo Breach, What's Changed? (Not Much)
Yahoo customers suffered the largest data breaches in history by some measures. But a decade on, experts warn, we still haven't learned our lesson.

2 Jan 2024
Biztonsági szemle
Microsoft hardens App Installer security as malware abuse continues
Less than a year after it re-emerged following earlier security issues, Microsoft has again taken action to limit malware distribution through its ms-appinstaller protocol for MSIX.
2 Jan 2024
Biztonsági szemle
Juniper Releases Security Advisory for Juniper Secure Analytics
Juniper released a security advisory to address multiple vulnerabilities affecting Juniper Secure Analytics. A cyber threat actor could exploit one of these vulnerabilities to take control of an affected system. CISA encourages users and...
Pagination
- Previous page ‹‹
- Page 1095
- Next page ››