Security Bulletin
9 Nov 2023
Biztonsági szemle
Hitachi Energy eSOMS
View CSAF 1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Hitachi Energy Equipment: eSOMS Vulnerabilities: Generation of Error Message Containing Sensitive Information, Exposure of Sensitive System...
9 Nov 2023
Biztonsági szemle
CISA Releases Four Industrial Control Systems Advisories
CISA released four Industrial Control Systems (ICS) advisories on November 9, 2023. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-23-313-01 Johnson Controls Quantum HD...
9 Nov 2023
Biztonsági szemle
Johnson Controls Quantum HD Unity
View CSAF 1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable Remotely/Low attack complexity Vendor: Johnson Controls Inc. Equipment: Quantum HD Unity Vulnerability: Active Debug Code 2. RISK EVALUATION Successful exploitation of this...
9 Nov 2023
Biztonsági szemle
CISA, NSA, and Partners Release New Guidance on Securing the Software Supply Chain
Today, CISA, the National Security Agency (NSA), and partners released Securing the Software Supply Chain: Recommended Practices for Software Bill of Materials Consumption. Developed through the Enduring Security Framework (ESF), this guidance...
9 Nov 2023
Biztonsági szemle
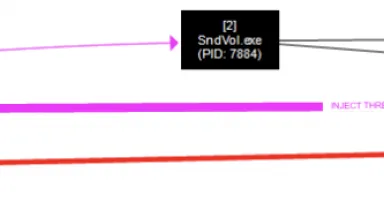
Visual Examples of Code Injection, (Thu, Nov 9th)
Code injection techniques (T1055 from MITRE[1]) is a common technique these days. It's a nice way for an attacker to hide malicious code into a legit process. A deviation of this technique is called âProcess Hollowingâ[2] where code of the...

9 Nov 2023
Biztonsági szemle
Sandworm Cyberattackers Down Ukrainian Power Grid During Missile Strikes
A premier Russian APT used living-off-the-land techniques in a major OT hit, raising tough questions about whether or not we can defend against the attack vector.

9 Nov 2023
Biztonsági szemle
Biden’s AI Executive Order: A temporary measure that emboldens our adversaries
We need to develop our own talent, find ways to protect IP, and play the long game on AI against the Chinese and other tech adversaries – we can’t do it with EOs and more regulations.

9 Nov 2023
Biztonsági szemle
ISC Stormcast For Thursday, November 9th, 2023 https://isc.sans.edu/podcastdetail/8738, (Thu, Nov 9th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

9 Nov 2023
Biztonsági szemle
Intern to DevNet Professional Certification: My Personal Journey
If, like Mohit, you enjoy both software development and networking, then Cisco DevNet certifications has plenty to offer by integrating network infrastructure with software applications, automation, and programmability. Here are Mohit's top...

9 Nov 2023
Biztonsági szemle
Step-by-step through the Money Message ransomware
Money Message is an insidious ransomware family known for resisting detection and remediation in various ways. We walk through a recent case.

8 Nov 2023
Biztonsági szemle
Evasive Jupyter Infostealer Campaign Showcases Dangerous Variant
The attacks are another manifestation of the concerning rise in information stealers for harvesting data and enabling persistent access to enterprise networks.

8 Nov 2023
Biztonsági szemle
Ransomware Mastermind Uncovered After Oversharing on Dark Web
Meet "farnetwork," one of the most prolific RaaS operators around, who spilled too many details during an affiliate "job interview."
Pagination
- Previous page ‹‹
- Page 1205
- Next page ››