Security Bulletin

6 Oct 2023
Biztonsági szemle
More than an Asset: The People Side of Mergers & Acquisitions
Thinking beyond the business case, why people are the critical asset in mergers and acquisitions.
6 Oct 2023
Biztonsági szemle
Apple Releases Security Updates for iOS and iPadOS
Apple has released security updates to address vulnerabilities in iOS and iPadOS. A cyber threat actor could exploit these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review the following...

6 Oct 2023
Biztonsági szemle
Understanding Client Classification
Most DHCP server administrators have heard or read about client classification. Unlike other DHCP server features, it is not described in any standards, but it is still one of the most widely used features in DHCP installations. The number of...

6 Oct 2023
Biztonsági szemle
ISC Stormcast For Friday, October 6th, 2023 https://isc.sans.edu/podcastdetail/8690, (Fri, Oct 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

5 Oct 2023
Biztonsági szemle
Spice up Cybersecurity Awareness Month with Free Security Tutorials in Cisco U.
Level up your security skills during Cybersecurity Awareness Month with fresh, new security tutorials. Get 'em while they're hot—or snack on them later. They'll be waiting for you inside Cisco U. Free.

5 Oct 2023
Biztonsági szemle
'Operation Jacana' Reveals DinodasRAT Custom Backdoor
The previously undocumented data exfiltration malware was part of a successful cyber-espionage campaign against the Guyanese government, likely by the Chinese.
5 Oct 2023
Biztonsági szemle
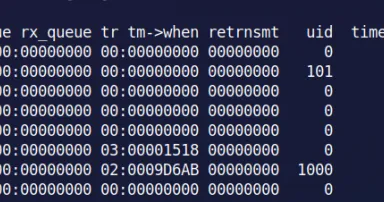
New tool: le-hex-to-ip.py, (Thu, Oct 5th)
So, this week it is my privilege to be TA-ing for Taz Wake for the beta run of his new class FOR577: Linux Incident Response and Threat Hunting. We were looking in the linux /proc filesystem and were noticing in the /proc/ /net/{tcp/udp/icmp/...}...

5 Oct 2023
Biztonsági szemle
Quash EDR/XDR Exploits With These Countermeasures
With tools and hacker groups constantly evading defenses, expanding cybersecurity beyond endpoint security becomes crucial.

5 Oct 2023
Biztonsági szemle
Legions of Critical Infrastructure Devices Subject to Cyber Targeting
Nearly 100,000 ICS devices have been found open to the public Internet, potentially threatening physical safety globally. Here's how to quantify the risk.

5 Oct 2023
Biztonsági szemle
10 Routine Security Gaffes the Feds Are Begging You to Fix
Here are the most common misconfigurations plaguing large organizations, according to a new joint cybersecurity advisory.

5 Oct 2023
Biztonsági szemle
Madagascar Drops Predator Spyware on Citizens in Watering Hole Attack
The Predator spyware was distributed by dropping malicious links inside typosquatted facsimiles of news websites.

5 Oct 2023
Biztonsági szemle
Group-IB: 'GoldDigger' Banking Trojan Targets Vietnamese Organizations
The malware uses software to evade detection while also making it difficult to analyze.
Pagination
- Previous page ‹‹
- Page 1276
- Next page ››