Security Bulletin

22 Jan 2026
Biztonsági szemle
AI Agents Undermine Progress in Browser Security
Web browser companies have put in substantial effort over the past three decades to strengthen the browser security stack against abuses. Agentic browsers are undoing all that work.

21 Jan 2026
Biztonsági szemle
'Contagious Interview' Attack Now Delivers Backdoor Via VS Code
Once trust is granted to the repository's author, a malicious app executes arbitrary commands on the victim's system with no other user interaction.

21 Jan 2026
Biztonsági szemle
Phishing Campaign Zeroes in on LastPass Customers
The bait incudes plausible subject lines and credible messages, most likely thanks to attackers' use of large language models to craft them.

21 Jan 2026
Biztonsági szemle
Cisco URWB: Powering Industrial AI & Automation on the Factory Floor
Discover how Cisco URWB powers industrial AI & automation for companies like E80 & Planet Farms, offering wireless reliability and operational simplicity.

21 Jan 2026
Biztonsági szemle
Complex VoidLink Linux Malware Created by AI
Researchers say the advanced framework was built almost entirely by agents, marking a significant evolution in the use of AI to develop wholly original malware.

21 Jan 2026
Biztonsági szemle
'Damn Vulnerable' Training Apps Leave Vendors' Clouds Exposed
Hackers are already leveraging these over-permissioned programs to access the IT systems of major security vendors.

21 Jan 2026
Biztonsági szemle
Riasztás az MVM Next Energiakereskedelmi Zrt. nevével visszaélő SMS üzenetekkel kapcsolatban
A Nemzetbiztonsági Szakszolgálat Nemzeti Kiberbiztonsági Intézet (NBSZ NKI) riasztást ad ki az MVM Next Energiakereskedelmi Zrt. nevével és arculati elemeivel visszaélő, adathalász hivatkozást tartalmazó szöveges üzenetek (SMS) terjedése kapcsán.

21 Jan 2026
Biztonsági szemle
CVE-2025-13878: Malformed BRID/HHIT records can cause named to terminate unexpectedly
CVE: CVE-2025-13878 Title: Malformed BRID/HHIT records can cause named to terminate unexpectedly Document version: 2.0 Posting date: 21 January 2026 Program impacted: BIND 9 Versions affected: BIND 9.18.40 -> 9.18.43 9.20.13 -> 9.20.17 9.21.12 -> 9...
21 Jan 2026
Biztonsági szemle
Join Cisco at the Rocky Mountain Cyberspace Symposium to unlock new possibilities for intelligent networks!
Join Cisco at the Rocky Mountain Cyberspace Symposium 2026 to experience hands-on AI, automation, and security innovations—plus live demos, expert sessions, and engaging activities designed to unlock your network’s full potential.

21 Jan 2026
Biztonsági szemle
Tájékoztatás a 2026. évi választásokkal összefüggésben
Tájékoztató a 2026. évi választásokkal összefüggésben.
21 Jan 2026
Biztonsági szemle
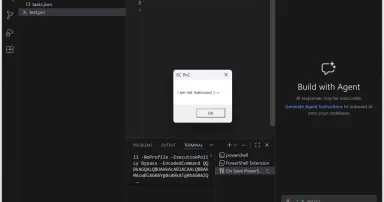
Automatic Script Execution In Visual Studio Code, (Wed, Jan 21st)
Visual Studio Code is a popular open-source code editor[ 1]. But it's much more than a simple editor, it's a complete development platform that supports many languages and it is available on multiple platforms. Used by developers worldwide...

21 Jan 2026
Biztonsági szemle
ISC Stormcast For Wednesday, January 21st, 2026 https://isc.sans.edu/podcastdetail/9774, (Wed, Jan 21st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Pagination
- Previous page ‹‹
- Page 16
- Next page ››