Security Bulletin

19 Dec 2025
Biztonsági szemle
ISC Stormcast For Friday, December 19th, 2025 https://isc.sans.edu/podcastdetail/9746, (Fri, Dec 19th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

18 Dec 2025
Biztonsági szemle
SonicWall Edge Access Devices Hit by Zero-Day Attacks
In the latest attacks against the vendor's SMA1000 devices, threat actors have chained a new zero-day flaw with a critical vulnerability disclosed earlier this year.

18 Dec 2025
Biztonsági szemle
Dark Reading Confidential: Stop Secrets Creep Across Developer Platforms
Dark Reading Confidential Episode 13: Developers are exposing their organizations' most sensitive information; our guests explain why it's happening and how to stop it.
18 Dec 2025
Biztonsági szemle
Modernizing Chip Manufacturing: Intel IT’s Journey with Cisco CX
Intel IT’s Sr. Director of Global Infrastructure Services and winner of the CX Customer Hero of the Year Award, shares how Cisco CX helped modernize their network infrastructure.

18 Dec 2025
Biztonsági szemle
12 Days of Learning: Your Secret to CCNA Momentum
Tune in for 12 Days of Learning, featuring expert-led prep, tips, hands-on practice guidance, and a chance to get certified for free.
18 Dec 2025
Biztonsági szemle
Scaling the World’s Most Sophisticated Networks: Q&A with Cisco VP Austin Lin
Discover how the unified Cisco Networking platform powers the world’s most sophisticated enterprises with unmatched scale, AgenticOps, and proven ROI.
18 Dec 2025
Biztonsági szemle
Transforming Wi-Fi Performance with AgenticOps: From Anxiety to Autonomy
Cisco AI-Enhanced RRM uses AI to optimize wireless networks, boosting reliability, speed, and efficiency while minimizing disruptions for users.

18 Dec 2025
Biztonsági szemle
OT Security Reimagined: From Legacy Limits to Network-Native Scale
Network-native OT security eliminates costly appliances and visibility gaps by embedding protection into the network, delivering comprehensive asset discovery and segmentation built for scale

18 Dec 2025
Biztonsági szemle
2025 in Review: Strengthening Cybersecurity in EMEA with AI
Reflecting on a transformative year for cybersecurity in EMEA. Discover how AI, regulation, and talent development shaped our digital future in 2025.

18 Dec 2025
Biztonsági szemle
Dormant Iran APT is Still Alive, Spying on Dissidents
"Prince of Persia" has rewritten the rules of persistence with advanced operational security and cryptographic communication with its command-and-control server.
18 Dec 2025
Biztonsági szemle
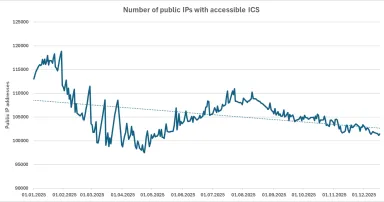
Positive trends related to public IP ranges from the year 2025, (Thu, Dec 18th)
Since the end of the year is quickly approaching, it is undoubtedly a good time to look back at what the past twelve months have brought to us⦠And given that the entire cyber security profession is about protecting various systems from âbad...

18 Dec 2025
Biztonsági szemle
ISC Stormcast For Thursday, December 18th, 2025 https://isc.sans.edu/podcastdetail/9744, (Thu, Dec 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Pagination
- Previous page ‹‹
- Page 29
- Next page ››