Security Bulletin

24 Mar 2025
Biztonsági szemle
US lifts Tornado Cash sanctions
Reuters reports that widely known cryptocurrency mixing service Tornado Cash had sanctions imposed by the Biden administration over its involvement in the laundering of over $7 billion for North Korean hackers and other cyber threat actors repealed...

24 Mar 2025
Biztonsági szemle
Widespread Keenetic router data breach uncovered
More than a million households, primarily in Russia, had their credentials, logs, network configurations, and other sensitive details leaked following the compromise of network equipment vendor Keenetic's Mobile App database, Cybernews reports.

24 Mar 2025
Biztonsági szemle
Virginia Attorney General's Office purportedly breached by Cloak ransomware
The Cloak ransomware operation has laid claim on a significant cyberattack against the Virginia Attorney General's Office last month, reports SecurityWeek.

24 Mar 2025
Biztonsági szemle
Credential exfiltration possible with Check Point ZoneAlarm driver bug
Threat actors have abused the vulnerable vsdatant.sys kernel-level driver within the Check Point ZoneAlarm antivirus version released in 2016 to exfiltrate account credentials as part of a Bring Your Own Vulnerable Driver attack, according to...

24 Mar 2025
Biztonsági szemle
Malware code-signed using Microsoft Trusted Signing service
Malware executables are being increasingly code-signed with three-day certificates using the Microsoft Trusted Signing service as threat actors seek to establish legitimacy and prevent thwarting by security systems, according to BleepingComputer.
24 Mar 2025
Biztonsági szemle
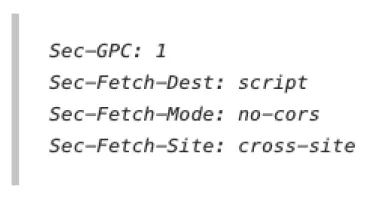
Privacy Aware Bots, (Mon, Mar 24th)
Staring long enough at honeypot logs, I am sure you will come across one or the other "oddity." Something that at first does not make any sense, but then, in some way, does make sense. After looking at the Next.js issue yesterday, I looked through...

24 Mar 2025
Biztonsági szemle
Cisco Co-Authors Update to the NIST Adversarial Machine Learning Taxonomy
Cisco and the UK AI Security Institute partnered with NIST to release the latest update to the Adversarial Machine Learning Taxonomy.

24 Mar 2025
Biztonsági szemle
Oracle Denies Claim of Oracle Cloud Breach of 6M Records
A threat actor posted data on BreachForums from an alleged supply chain attack that affected more than 140K tenants, claiming to have compromised the cloud via a zero-day flaw in WebLogic, researchers say.
24 Mar 2025
Biztonsági szemle
We need better detection feedback loops - Michael Mumcuoglu - ESW #399

24 Mar 2025
Biztonsági szemle
Is the Middle East's Race to Digitize a Threat to Infrastructure?
As the region continues with its ambitious road map, cybersecurity must be woven into every step of the process.

24 Mar 2025
Biztonsági szemle
ISC Stormcast For Monday, March 24th, 2025 https://isc.sans.edu/podcastdetail/9376, (Mon, Mar 24th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Pagination
- Previous page ‹‹
- Page 293
- Next page ››