Security Bulletin

12 Dec 2025
Biztonsági szemle
Supply Chain Attacks Targeting GitHub Actions Increased in 2025
At this week's Black Hat Europe conference, two researchers urged developers to adopt a shared responsibility model for open source software and not leave it all up to GitHub to handle.

12 Dec 2025
Biztonsági szemle
Have You Seen My Domain Controller?
Windows clients expose Active Directory DNS queries on public Wi-Fi, risking OSINT and credential leaks. Learn from Cisco Live SOC observations how to protect clients with VPNs .

12 Dec 2025
Biztonsági szemle
Are Trade Concerns Trumping US Cybersecurity?
The Trump administration appears to have dropped sanctions against Chinese actors for the Salt Typhoon attacks on US telecoms; but focusing on diplomacy alone misses the full picture, experts say.

12 Dec 2025
Biztonsági szemle
Splunk in Action: From SPL to PCAP
Learn how Cisco Live SOC uses Splunk SPL and Endace PCAP to investigate exposed HTTP authentication and Kerberos activity, securing sensitive data on public Wi-Fi networks.

12 Dec 2025
Biztonsági szemle
Cisco Live Melbourne 2025 SOC
Cisco Security and Splunk protected Cisco Live Melbourne 2025 in the Security Operations Centre. Learn about the latest innovations for the SOC of the Future.

12 Dec 2025
Biztonsági szemle
Sajtószemle – 2025. 50. hét
Megjelent a 2025. 50. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2025.12.05. és 2025.12.11. között kezelt incidensek, valamint az elosztott kormányzati IT biztonsági csapdarendszerből (GovProbe1) származó adatok statisztikai eloszlását is...

12 Dec 2025
Biztonsági szemle
Hamas-Linked Hackers Probe Middle Eastern Diplomats
Hamas's best hackers have been maturing, building better malware, and spreading their attacks more widely across the region.

12 Dec 2025
Biztonsági szemle
Riasztás Ivanti terméket érintő kritikus sérülékenységről
A Nemzetbiztonsági Szakszolgálat Nemzeti Kiberbiztonsági Intézet (NBSZ NKI) riasztást ad ki az Ivanti Endpoint Manager (EPM) szoftvert érintő kritikus kockázati besorolású sérülékenység kapcsán.

12 Dec 2025
Biztonsági szemle
Tájékoztatás Adobe szoftverek sérülékenységeiről – 2025. december
A Nemzetbiztonsági Szakszolgálat Nemzeti Kiberbiztonsági Intézet (NBSZ NKI) tájékoztatót ad ki az Adobe szoftverfejlesztő cég termékeit érintő sérülékenységekkel kapcsolatban, azok súlyossága, valamint az egyes biztonsági hibákat érintő aktív...

12 Dec 2025
Biztonsági szemle
Riasztás Microsoft termékeket érintő sérülékenységekről – 2025. december
A Nemzetbiztonsági Szakszolgálat Nemzeti Kiberbiztonsági Intézet (NBSZ NKI) riasztást ad ki a Microsoft szoftvereket érintő kritikus kockázati besorolású sérülékenységek kapcsán, azok súlyossága, kihasználhatósága és a szoftverek széleskörű...
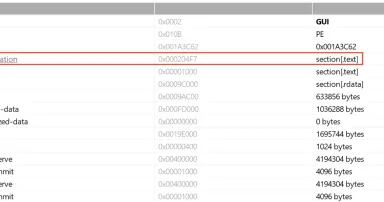
12 Dec 2025
Biztonsági szemle
Abusing DLLs EntryPoint for the Fun, (Fri, Dec 12th)
In the Microsoft Windows ecosystem, DLLs (Dynamic Load Libraries) are PE files like regular programs. One of the main differences is that they export functions that can be called by programs that load them. By example, to call RegOpenKeyExA(), the...

12 Dec 2025
Biztonsági szemle
ISC Stormcast For Friday, December 12th, 2025 https://isc.sans.edu/podcastdetail/9736, (Fri, Dec 12th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Pagination
- Previous page ‹‹
- Page 34
- Next page ››