Security Bulletin

25 Jan 2025
Biztonsági szemle
CCDE Evolves: New Specialist Certifications and AI Infrastructure Focus
As the demand for specialized network design skills in AI and automation continues to climb, important changes are coming to the Cisco Certified Design Expert (CCDE) program, effective February 9, 2025.

24 Jan 2025
Biztonsági szemle
CISOs Are Gaining C-Suite Swagger, but Has It Come With a Cost?
The number of CISOs who report directly to the CEO is up sharply in recent years, but many still say it's not enough to secure adequate resources.
24 Jan 2025
Biztonsági szemle
Attacks on Ivanti appliances demonstrate danger of chained exploits
CISA warned that attackers are chaining a number of CVE-listed vulnerabilities into a single exploit script.

24 Jan 2025
Biztonsági szemle
Reddit, WeTransfer pages spoofed in Lumma Stealer campaign
Nearly 1,000 imitation pages were discovered, targeting users looking for other software.

24 Jan 2025
Biztonsági szemle
Cursive Funk, Microsoft, Ivanti, Sonic Wall, Exchange, PowerSchool, Aaran Leyland... - SWN #445

24 Jan 2025
Biztonsági szemle
DoJ Busts Up Another Multinational DPRK IT Worker Scam
A departmentwide initiative has now led to five major law enforcement actions, in an attempt to curb the increasingly common trend of North Korean hackers posing as IT job applicants.

24 Jan 2025
Biztonsági szemle
QNAP patches six Rsync bugs that could lead to RCEs on NAS devices
Small and midsize companies tend not to check for NAS updates, so customers advised to patch right away.
24 Jan 2025
Biztonsági szemle
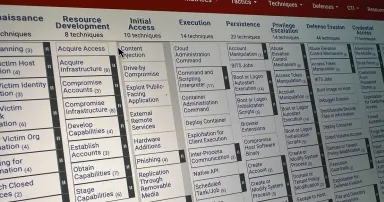
MITRE's Latest ATT&CK Simulations Tackle Cloud Defenses
The MITRE framework's applied exercise provides defenders with critical feedback about how to detect and defend against common, but sophisticated, attacks.

24 Jan 2025
Biztonsági szemle
Cisco: Critical Meeting Management Bug Requires Urgent Patch
The bug has been given a 9.9 CVSS score, and could allow authenticated threat actors to escalate their privileges to admin-level if exploited.

24 Jan 2025
Biztonsági szemle
3 Use Cases for Third-Party API Security
Third-party API security requires a tailored approach for different scenarios. Learn how to adapt your security strategy to outbound data flows, inbound traffic, and SaaS-to-SaaS interconnections.

24 Jan 2025
Biztonsági szemle
Strengthening Our National Security in the AI Era
For the first time in a long while, the federal government and the software sector alike finally have the tools and resources needed to do security well — consistently and cost-effectively.

24 Jan 2025
Biztonsági szemle
Most online Exchange Servers vulnerable to ProxyLogon still not remediated
Such lagging vulnerability remediation for ProxyLogon significantly contrasts patching activities for a pair of Ivanti flaws also leveraged in Salt Typhoon attacks, tracked as CVE-2023-46805 and CVE-2024-21887, which have been addressed in over 92%...
Pagination
- Previous page ‹‹
- Page 387
- Next page ››