Security Bulletin

18 Nov 2025
Biztonsági szemle
Can a Global, Decentralized System Save CVE Data?
As vulnerabilities in the Common Vulnerabilities and Exposures ecosystem pile up, one Black Hat Europe presenter hopes for a global, distributed alternative.

18 Nov 2025
Biztonsági szemle
Iran-Nexus Threat Actor UNC1549 Takes Aim at Aerospace
Researchers say Israel remains a central focus, with UNC1549 targeting aerospace and defense entities in the US, the UAE, Qatar, Spain, and Saudi Arabia.

18 Nov 2025
Biztonsági szemle
Cisco + BlueCat: Unified Branch for Smarter, Simpler Networking
Cisco Unified Branch and BlueCat Micetro unify networking, security, and DDI automation for consistent, AI-ready branch operations.

18 Nov 2025
Biztonsági szemle
How We Ditched the SaaS Status Quo for Time-Series Telemetry
Free the logs! Behind the scenes at InfluxData, which turned to its own in-house security monitoring platform, DiSCO, to protect its supply chain after its third-party tool was breached.

18 Nov 2025
Biztonsági szemle
The Peloton Approach to CCNA Exam Success
Quit the "Almost There" Club and cross the CCNA finish line with the help of AI.

18 Nov 2025
Biztonsági szemle
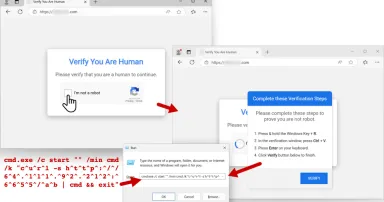
Malicious Npm Packages Abuse Adspect Cloaking in Crypto Scam
A malware campaign presents fake websites that can check if a visitor is a potential victim or a security researcher, and then proceed accordingly to defraud or evade.

18 Nov 2025
Biztonsági szemle
Bug Bounty Programs Rise as Key Strategic Security Solutions
Bug bounty programs create formal channels for organizations to leverage external security expertise, offering researchers legal protection and financial incentives for ethical vulnerability disclosure.

18 Nov 2025
Biztonsági szemle
Simplifying Conference Room Deployments with Catalyst 9200CX
The Cisco Catalyst 9200CX streamlines conference room setup by unifying AVoIP, networking, and Webex for secure, scalable hybrid collaboration.

18 Nov 2025
Biztonsági szemle
From Stretched to Strategic: Cisco Cloud Networking for Lean IT Teams
Discover how Cisco Cloud Networking transforms network management for lean SMB IT teams, offering unparalleled simplicity, centralized control, AI assistance, and integrated security to overcome daily challenges and drive strategic growth.

18 Nov 2025
Biztonsági szemle
Identity-Driven Firewalls: Shaping the Future of Adaptive Security
Active Directory compromises, credential theft, lateral movement. See how identity-driven security policies stop breaches before attackers escalate privileges.

18 Nov 2025
Biztonsági szemle
ISC Stormcast For Tuesday, November 18th, 2025 https://isc.sans.edu/podcastdetail/9704, (Tue, Nov 18th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Pagination
- Previous page ‹‹
- Page 48
- Next page ››