Security Bulletin

6 Nov 2024
Biztonsági szemle
Google Cloud mandates MFA by end of 2025
Security pros says the move to make MFA mandatory is long overdue.

6 Nov 2024
Biztonsági szemle
Google Cloud to Enforce MFA on Accounts in 2025
Google Cloud will take a phased approach to make multifactor authentication mandatory for all users.

6 Nov 2024
Biztonsági szemle
German Law Could Protect Researchers Reporting Vulns
The draft amendment also includes prison time for those who access systems to maliciously spy or intercept data.
6 Nov 2024
Biztonsági szemle
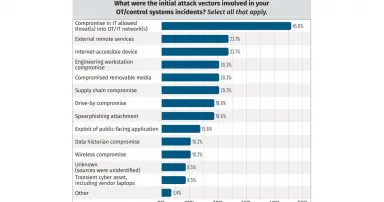
Attackers Breach IT-Based Networks Before Jumping to ICS/OT Systems
SANS recently published its 2024 State of ICS.OT Cybersecurity report, highlighting the skills of cyber professionals working in critical infrastructure, budget estimates, and emerging technologies. The report also looked at the most common types of...

6 Nov 2024
Biztonsági szemle
International Police Effort Obliterates Cybercrime Network
Interpol disrupts 22,000 malicious IP addresses, 59 servers, 43 electronic devices, and arrests 41 suspected cybercriminals.

6 Nov 2024
Biztonsági szemle
Despite Emerging Regulations, Mobile Device, IoT Security Requires More Industry Attention
Omdia Principal Analyst Hollie Hennessy says that until a promising new set of regulations around the world comes online, connected device security entails a shared responsibility among consumers, enterprises, and manufacturers.

6 Nov 2024
Biztonsági szemle
Nokia: No Evidence So Far That Hackers Breached Company Data
The mobile device maker continues to investigate IntelBroker's claims of another high-profile data breach, with the cybercriminal group posting on BreachForums internal data allegedly stolen from Nokia through a third-party contractor.

6 Nov 2024
Biztonsági szemle
New Army Cyber Command AI tool shows promise in bolstering Pentagon network defenses
Aside from enabling simultaneous network risk evaluations and threat intelligence delivery, Panopticon Junction has also allowed architecture-specific security assessments.

6 Nov 2024
Biztonsági szemle
Updated Strela Stealer malware hits Germany, Spain
Malicious emails purporting to be invoices that contain ZIP attachments have been delivered to facilitate the execution of a WebDAV-retrieved DLL that loads the updated Strela Stealer variant.

6 Nov 2024
Biztonsági szemle
US jails real estate phisher
The U.S. Department of Justice announced that Nigerian hacker Kolade Akinwale Ojelade has been sentenced to more than 26 years imprisonment for his involvement in a massive phishing scam against real estate businesses that resulted in the theft of...

6 Nov 2024
Biztonsági szemle
Dstat.cc DDoS platform disrupted in global crackdown
Pro-Russian hacktivist operations Killnet and Passion have leveraged Dstat.cc to promote their DDoS attack capabilities, with the latter touting its abilities to launch level 4 and level 7 intrusions, according to Germany's Federal Crime Police...

6 Nov 2024
Biztonsági szemle
Ransomware landscape dominated by RansomHub
Play, Qilin, Medusa, and LockBit — which was the dominant ransomware operation in 2022 and 2023 before being subjected to law enforcement crackdowns this year — completed the top five, according to an analysis from Check Point.
Pagination
- Previous page ‹‹
- Page 503
- Next page ››