Security Bulletin
2 Nov 2025
Biztonsági szemle
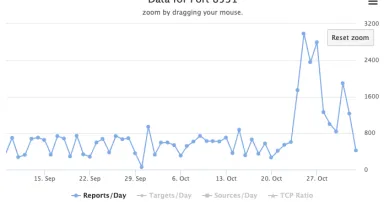
Scans for Port 8530/8531 (TCP). Likely related to WSUS Vulnerability CVE-2025-59287, (Sun, Nov 2nd)
Sensors reporting firewall logs detected a significant increase in scans for port 8530/TCP and 8531/TCP over the course of last week. Some of these reports originate from Shadowserver, and likely other researchers, but there are also some that do not...

31 Oct 2025
Biztonsági szemle
When the Cloud’s Backbone Falters: Why Digital Resilience Demands More Than Redundancy
On October 20, users around the world experienced the effects of a widespread AWS outage. In this article, we’ll explore why operations teams need multilayered assurance to understand their cloud dependencies and outline steps they can take now to...

31 Oct 2025
Biztonsági szemle
UNC6384 Targets European Diplomatic Entities With Windows Exploit
The spear-phishing campaign uses fake European Commission and NATO-themed lures to trick diplomatic personnel into clicking malicious links.

31 Oct 2025
Biztonsági szemle
Ribbon Communications Breach Marks Latest Telecom Attack
The US telecom company disclosed that suspected nation-state actors first gained access to its network in December of last year, though it's unclear if attackers obtained sensitive data.

31 Oct 2025
Biztonsági szemle
Government Approach to Disrupt Cyber Scams is 'Fragmented'
Users contend with cybersecurity scams throughout their day; a new Cyber Civic Engagement program wants to provide them with the skills to fight back.

31 Oct 2025
Biztonsági szemle
SecureBERT 2.0: Cisco’s next-gen AI model powering cybersecurity applications
Today, we are excited to share that the SecureBERT 2.0 model is available on HuggingFace and GitHub with an accompanying research paper. This release marks a significant milestone, building on the already widely adopted SecureBERT model to unlock...

31 Oct 2025
Biztonsági szemle
IPv6 in 2025 – Transitioning to IPv6
Discover how organizations are navigating the evolving landscape of IPv6, from dual-stack deployments to an IPv6-only future, and see how Cisco is guiding customers every step of the way..

31 Oct 2025
Biztonsági szemle
Sajtószemle – 2025. 44. hét
Megjelent a 2025. 44. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2025.10.22. és 2025.10.30. között kezelt incidensek, valamint az elosztott kormányzati IT biztonsági csapdarendszerből (GovProbe1) származó adatok statisztikai eloszlását is...

31 Oct 2025
Biztonsági szemle
Cyber's Role in the Rapid Rise of Digital Authoritarianism
Dark Reading Confidential Episode 11: Enterprise cyber teams are in prime position to push back against our current "Golden Age of Surveillance," according to our guests Ronald Deibert from Citizen Lab and David Greene from the EFF.

31 Oct 2025
Biztonsági szemle
ISC Stormcast For Friday, October 31st, 2025 https://isc.sans.edu/podcastdetail/9680, (Fri, Oct 31st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

31 Oct 2025
Biztonsági szemle
Zombie Projects Rise Again to Undermine Security
Companies left them for dead, but the remnants of old infrastructure and failed projects continue to haunt businesses' security teams.

30 Oct 2025
Biztonsági szemle
An 18-Year-Old Codebase Left Smart Buildings Wide Open
Researcher Gjoko Krstic’s "Project Brainfog" exposed hundreds of zero-day vulnerabilities in building-automation systems still running hospitals, schools, and offices worldwide.
Pagination
- Previous page ‹‹
- Page 60
- Next page ››