Security Bulletin

16 Sep 2024
Biztonsági szemle
Attacks leveraging Ivanti CSA vulnerability ongoing
The vulnerability, which impacts Ivanti CSA 4.6 that has recently reached end-of-life, could be leveraged to enable remote code execution, according to Ivanti, which urged immediate upgrades to Ivanti CSA 5.0.

16 Sep 2024
Biztonsági szemle
Updated TrickMo Android trojan emerges
Attacks involved the utilization of a fraudulent Google Chrome app, which when installed triggers a prompt for updating Google Play Services and eventually downloads TrickMo as "Google Services" before seeking the approval of accessibility...

16 Sep 2024
Biztonsági szemle
Novel malware attack conducts kiosk mode credential theft
Attacks as part of the campaign, which commenced in late August, involved the Amadey malware spreading a credential-flushing AutoIT script, which would launch a URL for replacing Google account passwords in kiosk mode and establish parameters that...

16 Sep 2024
Biztonsági szemle
Feds: US voter registration data breach claims false
Aside from noting that a potential compromise of publicly available voter registration details would not affect the process or results of the upcoming election, both the FBI and CISA emphasized that there has been no indication of any intrusion that...
16 Sep 2024
Biztonsági szemle
CISA Adds Two Known Exploited Vulnerabilities to Catalog
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-43461 Microsoft Windows MSHTML Platform Spoofing Vulnerability CVE-2024-6670 Progress WhatsUp Gold SQL Injection...
16 Sep 2024
Biztonsági szemle
New CISA Plan Aligns Federal Agencies in Cyber Defense
Today, the Cybersecurity and Infrastructure Security Agency (CISA) released the Federal Civilian Executive Branch (FCEB) Operational Cybersecurity Alignment (FOCAL) Plan. Developed in collaboration with FCEB agencies, this plan provides standard...

16 Sep 2024
Biztonsági szemle
How confidential computing protects 'data in use' for AI environments
Here are three tips for safeguarding confidential computing in AI environments.

16 Sep 2024
Biztonsági szemle
Managing PE Files With Overlays, (Mon, Sep 16th)
There is a common technique used by attackers: They append some data at the end of files (this is called an overlay). This can be used for two main reasons: To hide the appended data from the operating system (steganography). By example, you can...

16 Sep 2024
Biztonsági szemle
U.S. Tax Reform Can Fuel AI and Cybersecurity Innovation
As the U.S. Congress thinks about the parameters of a 2025 tax package, several areas could significantly shape innovation in AI and cybersecurity and serve as a catalyst for beneficial technology breakthroughs.

16 Sep 2024
Biztonsági szemle
ISC Stormcast For Monday, September 16th, 2024 https://isc.sans.edu/podcastdetail/9138, (Mon, Sep 16th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
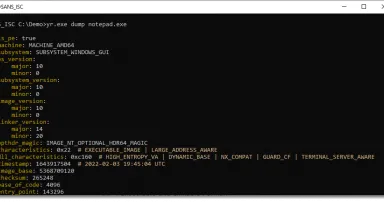
15 Sep 2024
Biztonsági szemle
YARA-X's Dump Command, (Sun, Sep 15th)
YARA-X is not just a rewrite of YARA in Rust, it comes with new features too.
Pagination
- Previous page ‹‹
- Page 600
- Next page ››