Security Bulletin

6 Aug 2025
Biztonsági szemle
What CMMC 3.0 Really Means for Government Contractors
The ultimate goal of CMMC 3.0 is not just compliance — it's resilience.

6 Aug 2025
Biztonsági szemle
Phishers Abuse Microsoft 365 to Spoof Internal Users
The "Direct Send" feature simplifies internal message delivery for trusted systems, and the campaign successfully duped both Microsoft Defender and third-party secure email gateways.

6 Aug 2025
Biztonsági szemle
Foundation-sec-8B-Instruct: An Out-of-the-Box Security Copilot
Foundation-sec-8B-Instruct layers instruction fine-tuning on top of our domain-focused base model, giving you a chat-native copilotthat understands security.

6 Aug 2025
Biztonsági szemle
SentinelOne Acquires AI Startup Prompt Security
The company will integrate Prompt Security's platform, which detects AI tools used in browsers and on desktops, into its Singularity platform.

6 Aug 2025
Biztonsági szemle
Hogyan ismerhetjük fel az online álláshirdetős csalásokat? – SANS OUCH! – 2025. augusztus
Megjelent a SANS és a Nemzetbiztonsági Szakszolgálat Nemzeti Kibervédelmi Intézet közös kiadványának 2025. augusztusi száma, melyben az online álláshirdetések veszélyeivel foglalkozunk. Bemutatjuk azt, hogy miért hatékonyak az ilyen típusú csalások...
6 Aug 2025
Biztonsági szemle
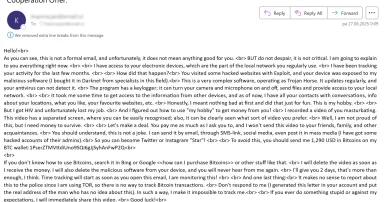
Do sextortion scams still work in 2025?, (Wed, Aug 6th)
Sextortion e-mails have been with us for quite a while, and these days, most security professionals tend to think of them more in terms of an âe-mail background noiseâ rather than as if they posed any serious threat. Given that their existence is...

6 Aug 2025
Biztonsági szemle
With Eyes on AI, African Orgs Push Security Awareness
Against the backdrop of the artificial intelligence surge, most African organizations have some form of cybersecurity awareness training but fail to test frequently and don't trust the results.

6 Aug 2025
Biztonsági szemle
To Raise or Not to Raise: Bootstrapped Founders Share Their Views
A trio of startup founders — GreyNoise's Andrew Morris, Thinkst Canary's Haroon Meer, and runZero's HD Moore — agree that raising venture capital funding can be beneficial, but a company's success depends on how well the product fits customer needs.

6 Aug 2025
Biztonsági szemle
ISC Stormcast For Wednesday, August 6th, 2025 https://isc.sans.edu/podcastdetail/9558, (Wed, Aug 6th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

5 Aug 2025
Biztonsági szemle
Pandora Confirms Third-Party Data Breach, Warns of Phishing Attempts
The jewelry retailer is warning customers that their data can and might be used maliciously.

5 Aug 2025
Biztonsági szemle
RCE Flaw in AI-Assisted Coding Tool Poses Software Supply Chain Risk
A critical vulnerability in the trust model of Cursor, a fast-growing tool for LLM-assisted development, allows for silent and persistent remote code execution.

5 Aug 2025
Biztonsági szemle
Cisco User Data Stolen in Vishing Attack
The networking giant said this week that an employee suffered a voice phishing attack that resulted in the compromise of select user data, including email addresses and phone numbers.
Pagination
- Previous page ‹‹
- Page 91
- Next page ››