Biztonsági szemle

2025. Júl. 29.
Biztonsági szemle
Supply Chain Attacks Spotted in GitHub Actions, Gravity Forms, npm
Researchers discovered backdoors, poisoned code, and malicious commits in some of the more popular tool developers, jeopardizing software supply chains.

2025. Júl. 29.
Biztonsági szemle
Lost, Found, and Flourishing: My Journey with Cisco
Read how Chirag G. went from self-doubt to finding confidence and a career path as a Cisco Software Engineering Intern, where one 'yes' changed everything.

2025. Júl. 29.
Biztonsági szemle
Triage is Key! Python to the Rescue!, (Tue, Jul 29th)
When you need to quickly analyze a lot of data, there is one critical step to perform: Triage. In forensic investigations, this step is critical because it allows investigators to quickly identify, prioritize, and isolate the most relevant or high...

2025. Júl. 29.
Biztonsági szemle
ISC Stormcast For Tuesday, July 29th, 2025 https://isc.sans.edu/podcastdetail/9546, (Tue, Jul 29th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

2025. Júl. 28.
Biztonsági szemle
Root Evidence Bets on New Concept for Vulnerability Patch Management
The number of concerning vulnerabilities may be much smaller than organizations think, and this cybersecurity startup aims to narrow down the list to the most critical ones.

2025. Júl. 28.
Biztonsági szemle
Insurance Giant Allianz Life Grapples With Breach Affecting 'Majority' of Customers
The company has yet to report an exact number of how many individuals were impacted by the breach and plans to start the notification process around Aug. 1.

2025. Júl. 28.
Biztonsági szemle
Chaos Ransomware Rises as BlackSuit Gang Falls
Researchers detailed a newer double-extortion ransomware group made up of former members of BlackSuit, which was recently disrupted by international law enforcement.

2025. Júl. 28.
Biztonsági szemle
Ghost Students Drain Money, Resources From Educational Sector
The education sector is haunted by a significant fraud problem where fake students impersonate celebrities and employ other identity techniques to steal resources and money from legitimate students.

2025. Júl. 28.
Biztonsági szemle
New Risk Index Helps Organizations Tackle Cloud Security Chaos
Enterprises can use the IaC Risk Index to identify vulnerable cloud resources in their infrastructure-as-code environment which are not managed or governed.

2025. Júl. 28.
Biztonsági szemle
Sophisticated Shuyal Stealer Targets 19 Browsers, Demonstrates Advanced Evasion
A new infostealing malware making the rounds can exfiltrate credentials and other system data even from browsing software considered more privacy-focused than mainstream options.
2025. Júl. 28.
Biztonsági szemle
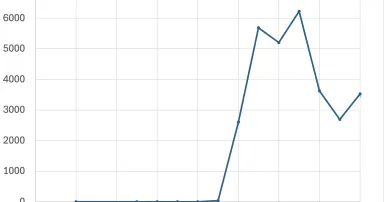
Parasitic Sharepoint Exploits, (Mon, Jul 28th)
Last week, newly exploited SharePoint vulnerabilities took a lot of our attention. It is fair to assume that last Monday (July 21st), all exposed vulnerable SharePoint installs were exploited. Of course, there is nothing to prevent multiple...

2025. Júl. 28.
Biztonsági szemle
Investing in AI & digital innovation for India’s farming future
The Cisco Foundation’s Regenerative Future Fund and Climate Grants Portfolio support tech ventures and nonprofits that are scaling reforestation, soil health, carbon markets, and nature-based solutions across India.
Oldalszámozás
- Előző oldal ‹‹
- 107. oldal
- Következő oldal ››