Biztonsági szemle

2025. Júl. 8.
Biztonsági szemle
Checking for Fraud: Texas Community Bank Nips Check Fraud in the Bud
Within months of implementing anti-fraud measures and automation, Texas National Bank prevented more than $300,000 in check fraud.

2025. Júl. 7.
Biztonsági szemle
Bert Blitzes Linux & Windows Systems
The new ransomware strain's aggressive multithreading and cross-platform capabilities make it a potent threat to enterprise environments.

2025. Júl. 7.
Biztonsági szemle
DPRK macOS 'NimDoor' Malware Targets Web3, Crypto Platforms
Researchers observed North Korean threat actors targeting cryptocurrency and Web3 platforms on Telegram using malicious Zoom meeting requests.

2025. Júl. 7.
Biztonsági szemle
Ransomware Attack Triggers Widespread Outage at Ingram Micro
The outage began shortly before the July 4 holiday weekend and caused disruptions for customer ordering and other services provided by the IT distributor.

2025. Júl. 7.
Biztonsági szemle
'Hunters International' RaaS Group Closes Its Doors
The announcement comes just months after security researchers observed that the group was making the transition to rebrand to World Leaks, a data theft outfit.

2025. Júl. 7.
Biztonsági szemle
How to Improve your eCommerce Strategy
Maximize SMB eCommerce success with AI, mobile-first strategies, and seamless customer journeys. Discover tips to boost conversions and stand out in a competitive market

2025. Júl. 7.
Biztonsági szemle
Chrome Store Features Extension Poisoned With Sophisticated Spyware
A color picker for Google's browser with more than 100,000 downloads hijacks sessions every time a user navigates to a new webpage and also redirects them to malicious sites.

2025. Júl. 7.
Biztonsági szemle
Cisco Contributes to Cyber Hard Problems Report
Cisco contributes to the latest edition of the Cyber Hard Problems report, highlighting 10 foundational security challenges facing the modern world.

2025. Júl. 7.
Biztonsági szemle
The case for replacing the secure email gateway
Here are five features to look for in a modern AI-based email security tool.
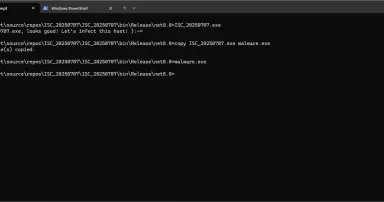
2025. Júl. 7.
Biztonsági szemle
What's My (File)Name?, (Mon, Jul 7th)
Modern malware implements a lot of anti-debugging and anti-analysis features. Today, when a malware is spread in the wild, there are chances that it will be automatically sent into a automatic analysis pipe, and a sandbox. To analyze a sample in a...

2025. Júl. 7.
Biztonsági szemle
ISC Stormcast For Monday, July 7th, 2025 https://isc.sans.edu/podcastdetail/9514, (Mon, Jul 7th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

2025. Júl. 6.
Biztonsági szemle
A few interesting and notable ssh/telnet usernames, (Sun, Jul 6th)
Just looked at our telnet/ssh honeypot data, and found some interesting new usernames that attackers attempted to use:
Oldalszámozás
- Előző oldal ‹‹
- 123. oldal
- Következő oldal ››