Biztonsági szemle

2025. Nov. 21.
Biztonsági szemle
With AI Reshaping Entry-Level Cyber, What Happens to the Security Talent Pipeline?
Automation is rewriting early-career cybersecurity work, raising urgent questions about how the next generation of security professionals will gain real-world expertise.

2025. Nov. 21.
Biztonsági szemle
Switching to Offense: US Makes Cyber Strategy Changes
The US national cyber director describes the next cyber strategy as focusing "on shaping adversary behavior," adding consequences and aggressive response.

2025. Nov. 21.
Biztonsági szemle
Sajtószemle – 2025. 47. hét
Megjelent a 2025. 47. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2025.11.14. és 2025.11.20. között kezelt incidensek, valamint az elosztott kormányzati IT biztonsági csapdarendszerből (GovProbe1) származó adatok statisztikai eloszlását is...
2025. Nov. 21.
Biztonsági szemle
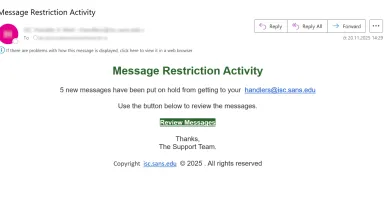
Use of CSS stuffing as an obfuscation technique?, (Fri, Nov 21st)
From time to time, it can be instructive to look at generic phishing messages that are delivered to one's inbox or that are caught by basic spam filters. Although one usually doesn't find much of interest, sometimes these little excursions...

2025. Nov. 21.
Biztonsági szemle
Inside Iran's Cyber Objectives: What Do They Want?
The regime's cyber-espionage strategy employs dual-use targeting, collecting info that can support both military needs and broader political objectives.

2025. Nov. 21.
Biztonsági szemle
ISC Stormcast For Friday, November 21st, 2025 https://isc.sans.edu/podcastdetail/9710, (Fri, Nov 21st)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

2025. Nov. 21.
Biztonsági szemle
Securing the Win: What Cybersecurity Can Learn From the Paddock
A Formula 1 pit crew demonstrates the basic principles of how modern security teams should work.

2025. Nov. 20.
Biztonsági szemle
CISOs Get Real About Hiring in the Age of AI
Dark Reading Confidential Episode 12: Experts help cyber job seekers get noticed, make an argument for a need to return to the hacker ethos of a bygone era, and have a stark conversation about keeping AI from breaking the sector's talent pipeline for...

2025. Nov. 20.
Biztonsági szemle
Chinese APT Infects Routers to Hijack Software Updates
A unique take on the software update gambit has allowed "PlushDaemon" to evade attention as it mostly targets Chinese organizations.

2025. Nov. 20.
Biztonsági szemle
Cisco U. Learning Deals 2025: One Week. Major Savings.
Get ready to shop and save big on Cisco learning.

2025. Nov. 20.
Biztonsági szemle
Same Old Security Problems: Cyber Training Still Fails Miserably
Editors from Dark Reading, Cybersecurity Dive, and TechTarget Search Security break down the depressing state of cybersecurity awareness campaigns and how organizations can overcome basic struggles with password hygiene and phishing attacks.

2025. Nov. 20.
Biztonsági szemle
‘Matrix Push’ C2 Tool Hijacks Browser Notifications
Have you ever given two seconds of thought to a browser notification? No? That's what hackers bent on phishing are counting on.
Oldalszámozás
- Előző oldal ‹‹
- 23. oldal
- Következő oldal ››