Biztonsági szemle

2025. Már. 26.
Biztonsági szemle
Misconfiguration leaks over 34M Sydney Tools order records
Major Australian trade tool retailer Sydney Tools had more than 34 million online order records and over 5,000 employees' records leaked by an unprotected ClickHouse database, according to Cybernews.

2025. Már. 26.
Biztonsági szemle
Mailchimp phishing exposes Have I Been Pwned subscribers
The Register reports that data breach notification service Have I Been Pwned had nearly 16,000 records belonging to current and former Mailchimp mailing list subscribers stolen following a successful phishing attack against HIBP Administrator Troy...

2025. Már. 26.
Biztonsági szemle
'Lucid' Phishing-as-a-Service Exploits Faults in iMessage, Android RCS
Cybercriminals in China have figured out how to undermine the strengths of mobile messaging protocols.

2025. Már. 26.
Biztonsági szemle
Beyond STIX: Next-Level Cyber-Threat Intelligence
While industry experts continue to analyze, interpret, and act on threat data, the complexity of cyber threats necessitates solutions that can quickly convert expert knowledge into machine-readable formats.

2025. Már. 26.
Biztonsági szemle
New Testing Framework Helps Evaluate Sandboxes
The Anti-Malware Testing Standards Organization published a Sandbox Evaluation Framework to set a standard among various sandbox offerings that help protect organizations from rising threats.

2025. Már. 26.
Biztonsági szemle
Striving for Sustainability: Meet Sripriya
Sripriya Narayanan is a senior product manager ho works for Cisco’s Industrial Internet of Things (IIoT) business unit, which focuses on industrial routers, switches, and access points. She has collaborated with Cisco’s Circular Design team to...

2025. Már. 26.
Biztonsági szemle
Unlocking the Power of Network Telemetry for the US Public Sector
Co-authors: Lou Norman and Erich Stokes A golden nugget can be seen as a valuable piece of information that significantly enhances security measures. In cybersecurity, identifying and leveraging such golden nuggets can be crucial for maintaining...

2025. Már. 26.
Biztonsági szemle
The Benefits of a Broad and Open Integration Ecosystem
Since inception, Cisco XDR has followed the Open XDR philosophy. We integrate telemetry and data from dozens of Cisco and third-party security solutions.

2025. Már. 26.
Biztonsági szemle
Google Hastily Patches Chrome Zero-Day Exploited by APT
Researchers at Kaspersky discovered cyber-espionage activity that used the vulnerability in a one-click phishing attack to deliver malware.

2025. Már. 26.
Biztonsági szemle
Public-Private Ops Net Big Wins Against African Cybercrime
Three cybersecurity firms worked with Interpol and authorities in Nigeria, South Africa, Rwanda, and four other African nations to arrest more than 300 cybercriminals.

2025. Már. 26.
Biztonsági szemle
ISC Stormcast For Wednesday, March 26th, 2025 https://isc.sans.edu/podcastdetail/9380, (Wed, Mar 26th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
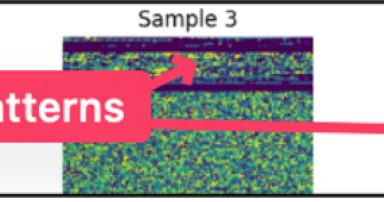
2025. Már. 26.
Biztonsági szemle
[Guest Diary] Leveraging CNNs and Entropy-Based Feature Selection to Identify Potential Malware Artifacts of Interest, (Wed, Mar 26th)
[This is a Guest Diary by Wee Ki Joon, an ISC intern as part of the SANS.edu Bachelor's Degree in Applied Cybersecurity (BACS) program [1].]
Oldalszámozás
- Előző oldal ‹‹
- 279. oldal
- Következő oldal ››