Biztonsági szemle

2025. Feb. 27.
Biztonsági szemle
DeepSeek-spoofing leveraged for crypto exfiltration
Nearly 40 domains have been created to facilitate intrusions distributing the Vidar malware.
2025. Feb. 27.
Biztonsági szemle
Generative AI Shows Promise for Faster Triage of Vulnerabilities
A host of automated approaches identifies and remediates potential vulns while still retaining a role for security analysts to filter for context and business criticality.
2025. Feb. 27.
Biztonsági szemle
Hackers Can Crack Into Car Cameras in Minutes Flat
It's shockingly simple to turn a car dashcam into a powerful reconnaissance tool for gathering everyday routine and location data, researchers warn.

2025. Feb. 27.
Biztonsági szemle
Cisco Live Melbourne SOC Report
Learn how the SOC team supported Cisco Live Melbourne and some of the more interesting findings from four days of threat hunting on the network.
2025. Feb. 27.
Biztonsági szemle
Dario Health USB-C Blood Glucose Monitoring System Starter Kit Android Application
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack complexity Vendor: Dario Health Equipment: USB-C Blood Glucose Monitoring System Starter Kit Android Application, Application Database and Internet-based Server...
2025. Feb. 27.
Biztonsági szemle
Schneider Electric Communication Modules for Modicon M580 and Quantum Controllers
View CSAF 1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Schneider Electric Equipment: Communication modules for Modicon M580 and Quantum controllers Vulnerability: Out-of-bounds Write 2. RISK...
2025. Feb. 27.
Biztonsági szemle
CISA Releases Two Industrial Control Systems Advisories
CISA released two Industrial Control Systems (ICS) advisories on February 27, 2025. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-25-058-01 Schneider Electric...
2025. Feb. 27.
Biztonsági szemle
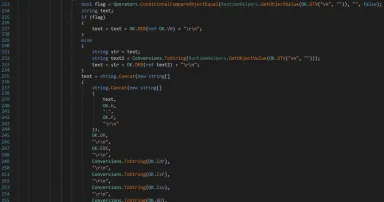
Njrat Campaign Using Microsoft Dev Tunnels, (Thu, Feb 27th)
I spotted new Njrat[ 1] samples that (ab)use the Microsoft dev tunnels[ 2] service to connect to their C2 servers. This is a service that allows developers to expose local services to the Internet securely for testing, debugging, and collaboration...

2025. Feb. 27.
Biztonsági szemle
Cybercriminals prefer remote tools over malware, says CrowdStrike
Remote tools allow data exfiltration without leaving a footprint or recognizable malware payload.

2025. Feb. 27.
Biztonsági szemle
ISC Stormcast For Thursday, February 27th, 2025 https://isc.sans.edu/podcastdetail/9342, (Thu, Feb 27th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
2025. Feb. 27.
Biztonsági szemle
OpenSSF Sets Minimum Security Baselines for Open Source Projects
OSPS Baseline provides a starting point for project owners and adopters to understand an open source project's security posture by outlining all the controls that have been applied.

2025. Feb. 27.
Biztonsági szemle
FDA Reinstates 'DOGED' Medical Device Staff Amid Cybersecurity, Health Concerns
Feds reverse order and reinstate FDA staff critical to medical device safety less than a week after firing them.
Oldalszámozás
- Előző oldal ‹‹
- 328. oldal
- Következő oldal ››