Biztonsági szemle

2025. Jan. 13.
Biztonsági szemle
Critical 10.0 Aviatrix Controller flaw exploited in the wild
Aviatrix Controllers are prime targets because they have high-level privileges in cloud environments.

2025. Jan. 13.
Biztonsági szemle
Cloud Attackers Exploit Max-Critical Aviatrix RCE Flaw
The security vulnerability tracked as CVE-2024-50603, which rates 10 out of 10 on the CVSS scale, enables unauthenticated remote code execution on affected systems, which cyberattackers are using to plant malware.
2025. Jan. 13.
Biztonsági szemle
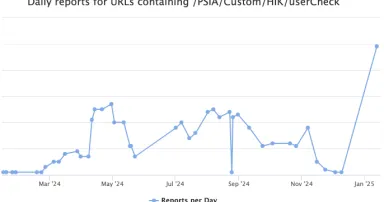
Hikvision Password Reset Brute Forcing, (Mon, Jan 13th)
One common pattern in password resets is sending a one-time password to the user to enable them to reset their password. The flow usually looks like:

2025. Jan. 13.
Biztonsági szemle
Cyberattackers Hide Infostealers in YouTube Comments, Google Search Results
Threat actors are targeting people searching for pirated or cracked software with fake downloaders that include infostealing malware such as Lumma and Vidar.

2025. Jan. 13.
Biztonsági szemle
Telefonica Breach Exposes Jira Tickets, Customer Data
The Hellcat ransomware group has stolen roughly 5,000 documents, potentially containing confidential information, from the telecom giant's internal database.

2025. Jan. 13.
Biztonsági szemle
Multicast fairness in high frequency trading environments
High Frequency Trading (HFT) customers demand real-time and fast connectivity to the exchange. Learn how to achieve multicast fairness with Nexus 3550-T and NX-OS for timely delivery of data and access to the exchange.

2025. Jan. 13.
Biztonsági szemle
Privacy Under Siege: Navigating Data Theft and the BadBox Threat - Gavin Reid - CSP #208

2025. Jan. 13.
Biztonsági szemle
The Shifting Landscape of Open Source Security
By focusing on vigilant security practices, responsible AI deployment, and alignment with global regulatory standards, the OSS community can make 2025 a transformative year for security.

2025. Jan. 13.
Biztonsági szemle
Redefining third-party governance and identity for the cloud-first era
Organizations are struggling to enforce security policies outside of traditional office environments, particularly concerning identity and access management, which is further complicated by the use of unsecured home networks and personal devices.

2025. Jan. 13.
Biztonsági szemle
Strengthening Cybersecurity: CMMC with Cisco’s NIST Cybersecurity Framework 2.0 Mapping
Discover how Cisco's security solutions align with NIST CSF 2.0 to support CMMC compliance, enhancing integration and protection against sophisticated cyber threats.

2025. Jan. 13.
Biztonsági szemle
The hybrid workforce crisis: How it has weakened enterprise security, and what to do about it
More robust identity and access management practices are crucial, especially as remote work environments often lack the security measures found in corporate settings.

2025. Jan. 13.
Biztonsági szemle
Data breach compromises STIIIZY customers' data
Infiltration of the vendor's systems between October and November exposed not only individuals' names, ages, and addresses, but also photographs, medical cannabis cards, driver's license numbers, and passport numbers, said STIIIZY in a breach notice...
Oldalszámozás
- Előző oldal ‹‹
- 403. oldal
- Következő oldal ››