Biztonsági szemle

2024. Dec. 26.
Biztonsági szemle
Almost 18K impacted by Texas university breach
Texas-based McMurry University had data from almost 18,000 individuals compromised as a result of a June data breach, Cybernews reports.

2024. Dec. 26.
Biztonsági szemle
Toll of American Addiction Centers hack surpasses 422K
Tennessee-based substance abuse treatment service provider American Addiction Centers had information from 422,424 individuals exfiltrated during a breach of its internal servers in September, which was initially disclosed to have affected 410,747...

2024. Dec. 26.
Biztonsági szemle
Ransomware hits Pittsburgh Regional Transit
Transit services at the Pittsburgh Regional Transit have resumed following a brief interruption last Thursday amid a ransomware intrusion, reports The Record, a news site by cybersecurity firm Recorded Future.

2024. Dec. 26.
Biztonsági szemle
Data exposed by over 30K Postman Workspace instances
Hackread reports that more than 30,000 internet-exposed instances of widely used cloud-based API development and testing platform Postman Workspace had API keys, tokens, and admin credentials exposed as a result of access control misconfiguration...

2024. Dec. 26.
Biztonsági szemle
Cyberattack defers Japan Airlines flights
Japan Airlines, the country's flag carrier, had over 20 domestic flights and some international trips delayed following a cyberattack, which also impacted ticket purchases and luggage services, Kyodo News reports.

2024. Dec. 26.
Biztonsági szemle
Widespread compromise possible Ruijie Networks cloud platform vulnerabilities
Nearly 50,000 Ruijie cloud-connected devices could be hijacked in attacks exploiting 10 security vulnerabilities in its Reyee cloud platform, all of which have already been patched, reports The Hacker News.

2024. Dec. 26.
Biztonsági szemle
Suspected Lazarus subgroup behind DMM crypto heist
U.S. and Japanese officials have attributed the massive $308 million cryptocurrency heist against Japanese cryptocurrency exchange DMM Bitcoin in May to North Korean threat operation TraderTraitor, which is believed to be a subgroup of the Lazarus...
2024. Dec. 26.
Biztonsági szemle
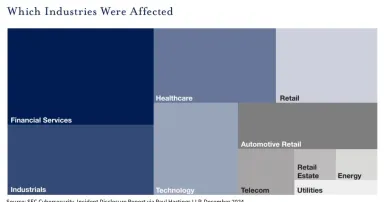
SEC Disclosures Up, But Not Enough Details Provided
While companies have responded to the new SEC rules by disclosing incidents promptly, many of the reports don't meet the SEC's "material" standard.

2024. Dec. 26.
Biztonsági szemle
Emerging Threats & Vulnerabilities to Prepare for in 2025
From zero-day exploits to 5G network vulnerabilities, these are the threats that are expected to persist over the next 12 months.

2024. Dec. 26.
Biztonsági szemle
How to reduce the typical 24-day recovery timeline
It often takes more than three weeks to recover from a cyberattack – here’s how to speed the process up.
2024. Dec. 26.
Biztonsági szemle
DDoS Attacks Surge as Africa Expands Its Digital Footprint
As organizations on the continent expand their use of digital technologies, they increasingly face many of the same threats that entities in other regions have had to deal with for years.
2024. Dec. 26.
Biztonsági szemle
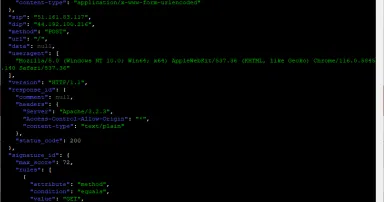
Capturing Honeypot Data Beyond the Logs, (Thu, Dec 26th)
By default, DShield Honeypots [1] collect firewall, web and cowrie (telnet/ssh) [2] data and log them on the local filesystem. A subset of this data is reported to the SANS Internet Storm Center (ISC) where it can be used by anyone [3]. A common...
Oldalszámozás
- Előző oldal ‹‹
- 423. oldal
- Következő oldal ››