Biztonsági szemle

2025. Okt. 22.
Biztonsági szemle
ISC Stormcast For Wednesday, October 22nd, 2025 https://isc.sans.edu/podcastdetail/9666, (Wed, Oct 22nd)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

2025. Okt. 22.
Biztonsági szemle
Asian Nations Ramp Up Pressure on Cybercrime 'Scam Factories'
After a particularly gruesome murder, South Korea issues "code black" travel ban for several regions in Cambodia, while other nations urge more raids.
2025. Okt. 22.
Biztonsági szemle
Dynamic AI Security: How Cisco AI Defense Protects Against New Threats
Introduction The pace at which applications for artificial intelligence are evolving continues to impress. Businesses that once considered taking advantage of AI’s sophisticated predictive and natural language capabilities are now evaluating adoption...

2025. Okt. 21.
Biztonsági szemle
Electronic Warfare Puts Commercial GPS Users on Notice
Interference with the global positioning system (GPS) isn't just a problem for airlines, but for shipping, trucking, car navigation, agriculture, and even the financial sector.

2025. Okt. 21.
Biztonsági szemle
Showcasing Innovation and Commitment at NetAcad’s European Partner Conference
Discover how Cisco NetAcad is preparing the European workforce for an AI-enabled future, training 1.5 million Europeans with foundational digital skills by 2030.

2025. Okt. 21.
Biztonsági szemle
Unleash(ed) AI: The Rise of Cognitive Security Operations
Discover how Cognitive Security, powered by agentic AI, transforms cyber defense. Learn how Cisco helps organizations move from reactive to proactive security operations. Explore now →

2025. Okt. 21.
Biztonsági szemle
New Investments, Stronger Grids: Elevating Rural Electric Cooperative Security
In towns and communities across the nation, rural electric cooperatives form the foundation of America’s power grid, delivering energy to millions of homes, businesses, and critical services. As the grid becomes more connected and digitized, these...

2025. Okt. 21.
Biztonsági szemle
Streaming Fraud Campaigns Rely on AI Tools, Bots
Fraudsters are using generative AI to generate fake music and boost the popularity of the fake content.

2025. Okt. 21.
Biztonsági szemle
5 Steps to Building Resilient Industrial Networks
Securing complex industrial environments can seem overwhelming. However, by adopting a structured, step-by-step approach, you can build a strong defense. Read this blog to discover Cisco’s 5-step framework to help you improve your industrial...
2025. Okt. 21.
Biztonsági szemle
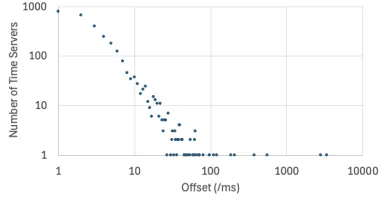
What time is it? Accuracy of pool.ntp.org., (Tue, Oct 21st)
Yesterday, Chinese security services published a story alleging a multi-year attack against the systems operating the Chinese standard time (CST), sometimes called Beijing Standard Time. China uses only one time zone across the country, and has not...

2025. Okt. 21.
Biztonsági szemle
Cisco Secure Firewall 1220: Snort3 – Uncompromised Performance in Rigorous Testing
This evaluation validates our commitment to delivering lightning-fast speed and impeccable protection, engineered to keep the most sophisticated threats away.

2025. Okt. 21.
Biztonsági szemle
‘PassiveNeuron’ Cyber Spies Target Orgs with Custom Malware
A persistent cyber espionage campaign focused on SQL servers is targeting government, industrial and financial sectors across Asia, Africa, and Latin America.
Oldalszámozás
- Előző oldal ‹‹
- 45. oldal
- Következő oldal ››