Biztonsági szemle
2024. Nov. 11.
Biztonsági szemle
How to Combat the CISO Mental Health Crisis - Ram Movva - BSW #372
2024. Nov. 11.
Biztonsági szemle
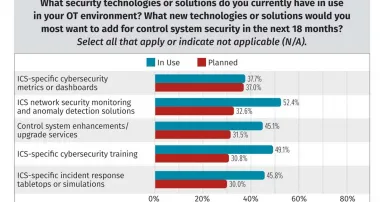
Incident Response, Anomaly Detection Rank High on Planned ICS Security Spending
The "SANS 2024 State of ICS/OT Cybersecurity" report suggests organizations are going to shift spending from security technologies protecting industrial control systems and operational technology environments to nontechnical activities, such as...

2024. Nov. 11.
Biztonsági szemle
Halliburton Remains Optimistic Amid $35M Data Breach Losses
Though its third-quarter earnings report confirms that the company remains on track, it's unclear how that will be affected if the threat actors commit further damage.

2024. Nov. 11.
Biztonsági szemle
Critical NAS-ty flaw strikes D-Link storage boxes
Organizations using D-Link network attached storage (NAS) hardware should check their devices following the disclosure of a critical security vulnerability
2024. Nov. 11.
Biztonsági szemle
'Top 10' malware strain, Remcos RAT, now exploiting Microsoft Excel files
Research underscores that many systems remain unpatched and are vulnerable to bugs that were patched several years ago.

2024. Nov. 11.
Biztonsági szemle
Revamped Remcos RAT Deployed Against Microsoft Windows Users
Windows users are at risk for full device takeover by an emerging malicious version of the Remcos remote admin tool, which is being used in an ongoing campaign exploiting a known remote code execution (RCE) vulnerability in Microsoft Office and...

2024. Nov. 11.
Biztonsági szemle
What Listening to My Father Taught Me About Cybersecurity
It's polite to listen to advice that people are willing to share, but not all of it will be useful for you. Here's how to separate the wheat from the chaff.
2024. Nov. 11.
Biztonsági szemle
Flexible Structure of Zip Archives Exploited to Hide Malware Undetected
Attackers abuse concatenation, a method that involves appending multiple zip archives into a single file, to deliver a variant of the SmokeLoader Trojan hidden in malicious attachments delivered via phishing

2024. Nov. 11.
Biztonsági szemle
Facebook Asks Supreme Court to Dismiss Cambridge Analytica Lawsuit
Meta has maintained that Facebook did not mislead investors by not including mention of the Cambridge Analytica scandal in its forward-looking risk disclosures, but the plaintiffs say it was a glaring omission.

2024. Nov. 11.
Biztonsági szemle
Open Source Security Incidents Aren't Going Away
Companies and organizations need to recognize the importance of investing in engineers who possess both the soft and hard skills required to secure open source software effectively.

2024. Nov. 11.
Biztonsági szemle
Robust Intelligence, Now Part of Cisco, Recognized as a 2024 Gartner® Cool Vendor™ for AI Security
Cisco is excited that Robust Intelligence, a recently acquired AI security startup, is mentioned in the 2024 Gartner Cool Vendors for AI Security report.

2024. Nov. 11.
Biztonsági szemle
How to capture that ‘sense of purpose’ in a cybersecurity career
Here are three tips that will help people better understand what led them to cybersecurity – and how to succeed.
Oldalszámozás
- Előző oldal ‹‹
- 495. oldal
- Következő oldal ››