Biztonsági szemle

2024. Aug. 19.
Biztonsági szemle
Flint city services disrupted by ransomware attack
While emergency and public health services, as well as public works activities, continue to be operational, the city's online and credit card systems have been taken down by the ransomware intrusion, noted officials.

2024. Aug. 19.
Biztonsági szemle
Sweeping data breach admitted by National Public Data
Such records — which were initially leaked by USDoD in April — may have included individuals' names, Social Security numbers, phone numbers, email addresses, and mailing addresses that were potentially compromised in a network breach in late December...
2024. Aug. 19.
Biztonsági szemle
Newly emergent Banshee Stealer extensively targets macOS systems
Banshee Stealer has been advertised to enable the theft of almost 100 browser extensions' data, iCloud Keychain credentials, and Notes, according to an Elastic Security Labs analysis.

2024. Aug. 19.
Biztonsági szemle
A Critical Look at the State Department's Risk Management Profile
The US needs to seize this moment to set a global standard for responsible and ethical AI, ensuring that technological progress upholds and advances human rights.

2024. Aug. 19.
Biztonsági szemle
Massive infostealer campaign exploits legitimate brands
Nearly 20 sub-campaigns have been part of Tusk, three of which remain active and leverage a Dropbox-hosted initial downloader to facilitate infostealer infections and personal and financial information compromise, an analysis from Kaspersky revealed.

2024. Aug. 19.
Biztonsági szemle
Iranian influence operation disrupted by OpenAI
Attackers also utilized ChatGPT to establish long-form articles and comments regarding Latinx rights in the U.S., the ongoing Israel-Gaza conflict, Israel's Olympic presence, Venezuelan politics, and Scottish independence, all of which have been...

2024. Aug. 19.
Biztonsági szemle
Widespread cloud extortion facilitated by misconfigured .ENV files
Inadequate protection of the .env files used for web app configuration variable definitions has enabled the compromise of AWS Identity and Access Management and eventual cloud environment access, according to an analysis from Palo Alto Networks.

2024. Aug. 19.
Biztonsági szemle
Assume Breach When Building AI Apps
AI jailbreaks are not vulnerabilities; they are expected behavior.
2024. Aug. 19.
Biztonsági szemle
CISA Adds One Known Exploited Vulnerability to Catalog
CISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-23897 Jenkins Command Line Interface (CLI) Path Traversal Vulnerability These types of vulnerabilities are...

2024. Aug. 19.
Biztonsági szemle
Five novel email phishing attacks – and what to do about them
Here’s an overview of the latest phishing attacks found by researchers – and three tips for mitigating them.
2024. Aug. 19.
Biztonsági szemle
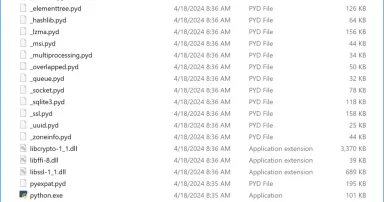
Do you Like Donuts? Here is a Donut Shellcode Delivered Through PowerShell/Python, (Mon, Aug 19th)
I found a tiny .bat file that looked not suspicious at all: 3650.bat (SHA256:bca5c30a413db21f2f85d7297cf3a9d8cedfd662c77aacee49e821c8b7749290) with a very low VirusTotal score (2/65)[ 1]. The file is very simple, it invokes a PowerShell:
Oldalszámozás
- Előző oldal ‹‹
- 657. oldal
- Következő oldal ››