Biztonsági szemle

2024. Aug. 1.
Biztonsági szemle
Black Basta Develops Custom Malware in Wake of Qakbot Takedown
The prolific ransomware group has shifted away from phishing as the method of entry into corporate networks, and is now using initial access brokers as well as its own tools to optimize its most recent attacks.

2024. Aug. 1.
Biztonsági szemle
Attackers Hijack Facebook Pages, Promote Malicious AI Photo Editor
A malvertising campaign uses phishing to steal legitimate account pages, with the endgame of delivering the Lumma stealer.

2024. Aug. 1.
Biztonsági szemle
The Cisco Store Retail Roundup, Volume 2
Explore all-new style guides and dive into the Cisco Store Tech Lab at Cisco Live.

2024. Aug. 1.
Biztonsági szemle
Fake Google Authenticator ads lure users to download malware on GitHub
Security pros caution users to download apps only from official app stores and websites.
2024. Aug. 1.
Biztonsági szemle
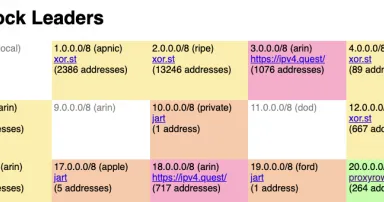
Tracking Proxy Scans with IPv4.Games, (Thu, Aug 1st)
Today, I saw a proxy scan that was a little bit different:

2024. Aug. 1.
Biztonsági szemle
A Commander’s-Intent-driven Network – Enabling Cyberspace Operations from the Tactical Edge and Beyond
Join us for AFCEA TechNet Augusta 2024 as we explore how people, processes, and technology shape the Cyber Domain. Be sure to visit our Solutions Review Session and Booth #105 as we propel Army Cyberspace Operations into the future.

2024. Aug. 1.
Biztonsági szemle
How Smart Tech is Teaching Us About Our Oceans, One Catch at a Time
Discover how smart technology is revolutionizing our understanding of the oceans and aiding fishermen, with innovative gear that collects vital data to help navigate changing seas and support sustainable fishing practices.

2024. Aug. 1.
Biztonsági szemle
Updated Opal Security platform strengthens IAM
Aside from new group optimization functionality that eases the removal of unneeded users and resources, Opal's platform has also been improved with more comprehensive irregular access screening that uses machine learning to better identify suspicious...

2024. Aug. 1.
Biztonsági szemle
Increased cookie protection, vulnerability patches introduced in Chrome update
Applications seeking cookie permissions will have their identities verified by App-Bound Encryption through a privileged service and would fail if similar data encoded into the encrypted data is decrypted by another app.
2024. Aug. 1.
Biztonsági szemle
Location-pointing vulnerability prevalent in dating apps
While all of the identified apps shared exact locations for their "filters" functionality, such an issue has already been addressed by the apps through the rounding up the exact coordinates that rendered oracle trilateration techniques ineffective.

2024. Aug. 1.
Biztonsági szemle
More patient data exfiltrated in Cencora breach
Major U.S. pharmaceutical firm Cencora has disclosed that more personal and protected health information had been stolen than initially reported during a February cyberattack against a patient support services subsidiary.

2024. Aug. 1.
Biztonsági szemle
Chinese malware attacks targeted at Japan
Attacks by Cuckoo Spear may have involved the utilization of LODEINFO, which allows file theft, arbitrary shellcode execution, keystroke logging, process termination, and screenshot capturing, as an initial payload.
Oldalszámozás
- Előző oldal ‹‹
- 692. oldal
- Következő oldal ››