Biztonsági szemle

2025. Aug. 15.
Biztonsági szemle
Water Systems Under Attack: Norway, Poland Blame Russia Actors
Water and wastewater systems have become a favored target of nation-state actors, drawing increasing scrutiny following attacks on systems in multiple countries.

2025. Aug. 15.
Biztonsági szemle
Sajtószemle – 2025. 33. hét
A 2025. 33. hetére vonatkozó hírválogatás, amely az NBSZ NKI által 2025.08.08. és 2025.08.14. között kezelt incidensek statisztikai adatait is tartalmazza.

2025. Aug. 15.
Biztonsági szemle
ISC Stormcast For Friday, August 15th, 2025 https://isc.sans.edu/podcastdetail/9572, (Fri, Aug 15th)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
2025. Aug. 15.
Biztonsági szemle
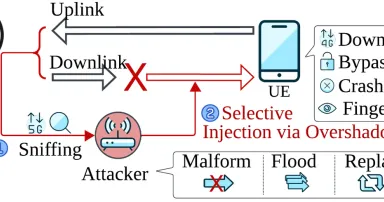
SNI5GECT: Sniffing and Injecting 5G Traffic Without Rogue Base Stations, (Thu, Aug 14th)
As the world gradually adopts and transitions to using 5G for mobile, operational technology (OT), automation and Internet-of-Things (IoT) devices, a secure 5G network infrastructure remains critical. Recently, the Automated Systems SEcuriTy (ASSET)...

2025. Aug. 14.
Biztonsági szemle
Downgrade Attack Allows Phishing Kits to Bypass FIDO
You probably can't break FIDO authentication. Still, researchers have shown that there are ways to get around it.

2025. Aug. 14.
Biztonsági szemle
State and Local Leaders Lobby Congress for Cybersecurity Resources
Federal funding cuts to the Multi-State Information Sharing and Analysis Center (MS-ISAC) are about to leave more than 18,000 state and local organizations without access to basic cybersecurity resources they need to protect US national security, a...

2025. Aug. 14.
Biztonsági szemle
Agentic AI Use Cases for Security Soar, but Risks Demand Close Attention
Organizations increasingly use agents to automate mundane tasks and address an overwhelming amount of sensitive data. However, adoption requires strict security strategies that keep humans in the loop for now.

2025. Aug. 14.
Biztonsági szemle
Google Chrome Enterprise: Advanced Browser Security for the Modern Workforce
In this Dark Reading News Desk interview, Google's Mark Berschadski highlights the critical role browsers play in today's work environment and how Chrome Enterprise is evolving to meet modern security challenges while enabling productivity.

2025. Aug. 14.
Biztonsági szemle
Police & Government Email Access for Sale on Dark Web
Cybercriminals are auctioning off live email credentials, giving other criminals access to sensitive systems, confidential intelligence, and, potentially, a higher success rate than ever.

2025. Aug. 14.
Biztonsági szemle
NIST Digital Identity Guidelines Evolve With Threat Landscape
The US National Institute of Standards and Technology updated its Digital Identity Guidelines to match current threats. The document detailed technical recommendations as well as suggestions for organizations.

2025. Aug. 14.
Biztonsági szemle
CISA Warns N-able Bugs Under Attack, Patch Now
Two critical N-able vulnerabilities enable local code execution and command injection; they require authentication to exploit, suggesting they wouldn't be seen at the beginning of an exploit chain.

2025. Aug. 14.
Biztonsági szemle
Cybersecurity Spending Slows & Security Teams Shrink
Security budgets are lowest in healthcare, professional and business services, retail, and hospitality, but budget growth remained above 5% in financial services, insurance, and tech.
Oldalszámozás
- Előző oldal ‹‹
- 93. oldal
- Következő oldal ››